What Is An Open Proxy: Risks and Uses

Welcome to our article on open proxies! In this section, we will explore the concept of an open proxy and its functions. We will provide a detailed explanation of what an open proxy is and how it is used as a proxy server.
So, what is an open proxy? Essentially, an open proxy is a server that acts as an intermediary between you and the internet. It allows you to send and receive data while preserving your anonymity. Open proxies are often used for various purposes, such as accessing blocked websites, bypassing content filters, or hiding your true IP address.
Understanding the usage of open proxies is crucial, as it helps you protect your online privacy and security. However, it’s essential to be aware of the risks associated with open proxies. Hackers and cybercriminals often exploit open proxies to carry out malicious activities, such as stealing sensitive information or spreading malware.
In the next sections, we will delve into the different types of proxies, highlight the vulnerabilities associated with proxy servers, and explore the internet security risks involved in using open proxies. We will also provide valuable tips on detecting if an open proxy is being used and offer insights into safe internet usage and online privacy.
Stay tuned as we uncover the world of open proxies and equip you with the knowledge to protect yourself online!
Types of Proxies
In this section, we will explore the different types of proxies that exist and their functionalities. A proxy server acts as an intermediary between a user’s device and the internet, enhancing privacy and security. Understanding the various categories of proxies is essential in determining their suitability for specific needs.
1. Transparent Proxies
Transparent proxies, also known as intercepting proxies, do not modify any data as it passes through. They are commonly used by organizations to monitor and control internet usage. While transparent proxies don’t provide anonymity, they can assist in filtering web content.
2. Anonymous Proxies
Anonymous proxies conceal the user’s IP address, making it challenging to trace online activities back to them. They offer a moderate level of privacy, making them popular among individuals who want to bypass geolocation restrictions or access region-specific content.
3. Elite Proxies
Elite proxies, also referred to as high-anonymity proxies, provide the highest level of privacy. They not only hide the user’s IP address but also manipulate HTTP headers, making it challenging to detect proxy usage. Elite proxies are often used for activities requiring maximum anonymity and security.
While proxies offer benefits such as improved privacy and access to restricted content, it’s crucial to note that proxy servers can also have vulnerabilities. These vulnerabilities can expose users to various risks, including data breaches and malware infections.
Next, we will explore the internet security risks associated with using open proxies.
Internet Security Risks
When it comes to using open proxies, there are several internet security risks that individuals should be aware of. These risks can have serious consequences, including data theft, malware infections, and identity theft. It’s crucial to understand these risks and take the necessary precautions to protect yourself online.
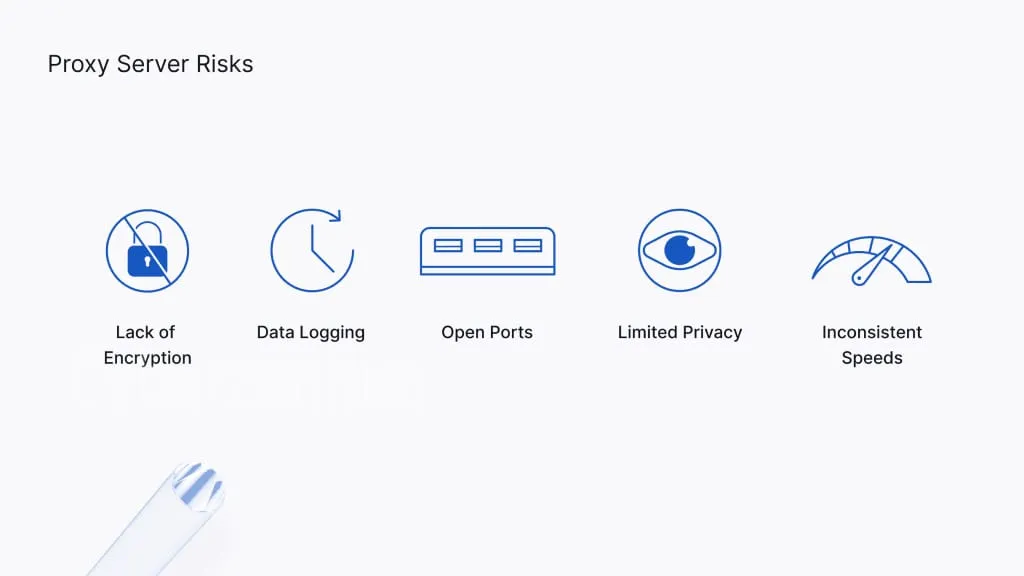
1. Data Theft
- Using an open proxy exposes your data to potential interception. Hackers can easily capture sensitive information such as passwords, credit card details, and personal documents.
- Be cautious when transmitting sensitive information over an open proxy, as it may not provide the necessary encryption to keep your data secure.
2. Malware Infections
- Open proxies can act as gateways for malware infections. Cybercriminals may inject malicious code into the proxy server, which can then infect your device when you connect.
- Malware can cause significant damage, including data loss, system crashes, and unauthorized access to your device or network.
3. Identity Theft
- Using an open proxy increases the risk of identity theft. Cybercriminals can potentially obtain your personal information, such as your name, address, and social security number, through insecure proxy connections.
- Once your identity is stolen, it can be used to commit various fraudulent activities, including financial fraud and impersonation.
How to Detect Open Proxy Usage?
- There are several signs that indicate the use of an open proxy:
- Unexpected browser behavior, such as frequent redirects or unusual advertisements
- Slow internet connection speed
- Inconsistent IP addresses when browsing different websites
- Difficulty accessing certain websites or web services
It’s important to stay vigilant and be proactive in detecting and avoiding open proxies. By understanding the risks involved and taking the necessary precautions, you can help protect your online security and safeguard your personal information.
Safe Internet Usage and Online Privacy
In today’s digital age, ensuring safe internet usage and prioritizing online privacy has become crucial.
The Importance of Protecting Online Privacy
With the increasing prevalence of online threats and data breaches, safeguarding your personal information is of utmost importance. Online privacy refers to the ability to control what information you share online and who has access to it. Protecting your online privacy helps prevent identity theft, data leaks, and unauthorized access to your sensitive information.
Measures to Protect Online Privacy
To maintain online privacy, you can take several proactive measures:
- Use a Virtual Private Network (VPN): A VPN encrypts your internet connection, making it more secure and private. It masks your IP address, allowing you to browse the internet anonymously.
- Avoid Suspicious Websites: Be cautious when visiting unfamiliar websites or downloading files from untrusted sources. Malicious websites and files can compromise your online privacy and expose your personal information.
- Practice Safe Browsing Habits: Be mindful of the websites you visit and the information you share online. Avoid clicking on suspicious links or providing sensitive data on unsecured websites.
Additional Steps for Online Privacy
Here are a few additional steps you can take to enhance your online privacy:
- Regularly Update Your Software: Keeping your operating system, web browser, and security software up to date ensures you benefit from the latest security patches and safeguards your devices from vulnerabilities.
- Manage Your Online Presence: Review your social media privacy settings and limit the amount of personal information you share publicly. Be mindful of the photos, posts, and comments you share, as they can impact your online privacy.
- Use Strong and Unique Passwords: Create passwords that are difficult to guess and avoid using the same password for multiple accounts. Consider using a password manager to securely store and manage your passwords.
By implementing these measures and being mindful of your online behavior, you can significantly enhance your online privacy and protect yourself from potential threats.
Conclusion
In conclusion, understanding open proxies is crucial for maintaining online security and privacy. Throughout this article, we have explored the concept of open proxies, their different types, and the associated risks.
Open proxies, though they can provide certain benefits such as anonymous browsing, come with significant vulnerabilities. These vulnerabilities include the potential for data theft, malware infections, and identity theft. It is important to be aware of these risks in order to protect oneself from potential harm.
To prioritize online security and privacy, it is recommended to practice safe internet usage. This includes utilizing secure connections, avoiding suspicious websites, and being cautious of the information shared online. Additionally, employing a reliable virtual private network (VPN) can further enhance online privacy and protect against potential threats.
In a world where online threats continue to evolve, it is essential to stay informed and vigilant. By adopting safe internet practices and understanding the risks associated with open proxies, individuals can safeguard their personal information and enjoy a secure online experience.
FAQ
What is an open proxy?
An open proxy is a server that allows users to route their internet traffic through it, acting as an intermediary between the user and the websites they visit. It can be accessed by anyone and is not restricted to a specific user or network.
How does an open proxy work as a proxy server?
When you connect to the internet through an open proxy, your requests are sent to the server, which then relays them to the intended website. This process masks your original IP address, providing you with a certain level of anonymity.
What are the risks associated with using open proxies?
Using open proxies can pose several risks, such as the theft of sensitive data, malware infections, and even identity theft. Since open proxies can be accessed by anyone, malicious individuals can exploit them to intercept and manipulate your internet traffic.
How can I detect if an open proxy is being used?
There are several methods to detect if an open proxy is being used, such as monitoring your network traffic for suspicious activity or using online proxy detection services. Additionally, you can check your internet connection settings to see if any proxy configurations are present.
What are the different types of proxies?
There are various types of proxies, including transparent proxies, which do not modify your requests; anonymous proxies, which hide your IP address but may still reveal other information; and elite proxies, which provide the highest level of anonymity by concealing all your details.
What are the vulnerabilities associated with proxy servers?
Proxy servers can be vulnerable to security breaches, allowing hackers to gain unauthorized access to the server and potentially the connected devices. Configuration errors, outdated software, and poor security practices can all contribute to these vulnerabilities.
How can I protect my online privacy?
To protect your online privacy, consider using a reliable virtual private network (VPN), which encrypts your internet traffic and hides your IP address. Additionally, practice safe browsing habits, avoid suspicious websites, and regularly update your devices and software.
