In today’s digital age, where online privacy and security are more critical than ever, choosing the best vpn for 2023 is essential for anyone looking to protect their data, bypass geo-restrictions, and enjoy uninterrupted internet access. With cyber threats evolving rapidly and internet service providers (ISPs) monitoring online activities, a reliable best vpn for 2023 acts as a shield against these risks. This article will explore the features that define the best vpn for 2023, highlight top contenders in the market, and guide you through the decision-making process to find the perfect fit for your needs. Why a Good VPN is Essential in 2023 The Growing Threat to Online Privacy The best vpn for 2023 isn’t just a luxury—it’s a necessity. As cyberattacks increase in frequency and sophistication, individuals and businesses face significant risks of data breaches, identity theft, and surveillance. Whether you’re streaming content, shopping online, or accessing sensitive information, a best vpn for 2023 encrypts your data and masks your IP address, ensuring that your online activities remain private. Bypassing Geo-Restrictions and Censorship Another key reason to invest in the best vpn for 2023 is its ability to bypass geo-restrictions. Streaming platforms, social media, and websites often limit access based on location, but a best vpn for 2023 allows you to connect to servers in different countries, granting you unlimited access to global content. This is particularly useful for travelers, remote workers, and users in regions with strict internet censorship. While security is paramount, speed is equally important. A best vpn for 2023 should not only protect your data but also provide a smooth browsing experience. Slow connections can frustrate users, especially when streaming high-definition videos or downloading large files. The best vpn for 2023 balances robust encryption with high-speed performance, ensuring that you don’t compromise on speed for security. Key Features to Look for in the Best vpn for 2023 Strong Encryption and Privacy Protection The best vpn for 2023 should prioritize strong encryption to safeguard your data. AES-256 encryption is the gold standard in this regard, as it’s virtually unbreakable with current technology. Additionally, a no-logs policy is crucial, as it ensures that the best vpn for 2023 doesn’t store any information about your online activities, including browsing history and connection timestamps. This feature is especially important for users who value complete anonymity. Italic encryption protocols like OpenVPN, IKEv2, and WireGuard also play a role in determining the speed and security of a best vpn for 2023. While OpenVPN is widely trusted for its security, WireGuard offers faster performance, making it an ideal choice for users who need quick access to the internet. Global Server Network and Server Locations A best vpn for 2023 with a global server network allows you to connect to servers in multiple regions, which is essential for bypassing censorship and accessing localized content. For example, if you’re in Asia and want to stream a European TV show, a best vpn for 2023 with servers in Europe will enable seamless access. Moreover, the number of servers in a region affects performance. A best vpn for 2023 with a large server network reduces congestion, ensuring faster speeds and more stable connections. This is particularly beneficial for users who frequently switch between locations or require access to multiple streaming services. Speed and Bandwidth Limitations One of the most common complaints about traditional VPNs is their impact on internet speed. However, the best vpn for 2023 is designed to minimize this effect. Look for a provider that offers unlimited bandwidth and fast connection speeds. This ensures that you can stream, download, or work online without experiencing lag or buffering. Italic speed is also influenced by the distance between your location and the server you connect to. The best vpn for 2023 should allow you to choose servers close to your current position to reduce latency and improve performance. Additionally, features like split tunneling and kill switches enhance speed and reliability by directing traffic through the VPN or disconnecting you automatically if the connection drops. Compatibility and User-Friendliness The best vpn for 2023 should be compatible with your devices and operating systems. Whether you’re using a Windows PC, Mac, iOS, or Android, a reliable best vpn for 2023 offers seamless integration across platforms. User-friendliness is another critical factor. The best vpn for 2023 should have an intuitive interface, making it easy for both tech-savvy users and beginners to set up and manage. Features like automatic server selection, quick connect, and customer support contribute to an effortless experience. Top Picks for the Best vpn for 2023 NordVPN: The Ultimate Security Leader NordVPN is often cited as one of the best vpn for 2023 for its cutting-edge security and extensive server network. With over 5,000 servers in 59 countries, NordVPN ensures that users can access unlimited access to global content without compromising speed. The best vpn for 2023 also boasts double encryption, which adds an extra layer of protection for sensitive data. Additionally, NordVPN offers zero-logs policy, making it a top choice for privacy-conscious individuals. Its user-friendly apps and split tunneling feature allow users to customize their connections, ensuring optimal performance for specific tasks. ExpressVPN: Fast and Reliable Performance If speed is your priority, ExpressVPN is a strong contender as one of the best vpn for 2023. Known for its high-speed connections, ExpressVPN delivers unlimited access with minimal latency, even on high-demand servers. The best vpn for 2023 also provides strong encryption and robust privacy features, including no-logs policy and kill switch. With a global network of 94 servers in 30 countries, ExpressVPN is ideal for users who need fast access to streaming platforms or online gaming services. Its apps are sleek and easy to use, making it a popular choice for both casual and professional users. CyberGhost: Affordable and Feature-Rich For budget-conscious users, CyberGhost stands out as one of the best vpn for 2023. It offers unlimited access to the internet at an affordable price, making it accessible to a wide range of users. The best
Best VPN for Streaming Services 2024 – Ultimate Guide
In today’s digital age, streaming services have become a cornerstone of entertainment, offering everything from Netflix and HBO Max to Disney+ and Amazon Prime Video. However, many users face challenges like geo-restrictions, buffering issues, and data privacy concerns when accessing these platforms. This is where the best vpn for streaming services comes into play. A reliable VPN (Virtual Private Network) can unlock a world of content, enhance security, and ensure uninterrupted streaming. With so many VPN providers on the market, selecting the best vpn for streaming services in 2024 requires careful consideration of factors like speed, server locations, and compatibility with popular platforms. Whether you’re a streaming enthusiast or a digital nomad looking to access content from anywhere, this guide will help you identify the top VPNs that deliver the best performance for streaming. Why a Good VPN is Essential for Streaming Services Bypass Geo-Restrictions and Unlock Global Content One of the primary reasons users turn to the best vpn for streaming services is to bypass geo-restrictions. Streaming platforms often limit content based on your location, meaning you might not see the same shows or movies as someone in another country. By connecting to a VPN server in a different region, you can mask your IP address and access global content libraries. This is particularly useful for Netflix, which varies its available titles by country, or Disney+, which has different content offerings depending on your location. Enhance Security and Privacy While streaming services are convenient, they often collect user data, including viewing habits and device information. A reliable VPN adds an extra layer of security by encrypting your internet traffic and protecting your online identity. This is especially important if you’re using public Wi-Fi or sharing your account with others. The best vpn for streaming services should have strong encryption protocols, a no-logs policy, and robust security features to ensure your data remains private. Overcome Bandwidth Limitations and Improve Speed Another key benefit of using a VPN for streaming is overcoming bandwidth limitations. Some internet service providers (ISPs) throttle streaming traffic, especially when you’re watching high-definition content. A fast and reliable VPN can bypass these throttling techniques by routing your connection through optimized servers. This ensures smooth playback, low latency, and no buffering during your favorite shows or movies. Access Multiple Streaming Platforms Simultaneously Many VPNs allow you to connect multiple devices at once, making it easier to stream content across your smartphone, tablet, and computer. This is ideal for households or users who want to watch on different devices without having to log in repeatedly. The best vpn for streaming services should support multi-device connectivity and integrate seamlessly with popular streaming apps, ensuring a seamless experience regardless of your device type. Top Contenders for 2024: The Best VPNs for Streaming Services NordVPN – Reliable Performance and Strong Privacy NordVPN has long been a top contender in the best vpn for streaming services category. It offers over 5,000 servers worldwide, ensuring fast and stable connections for high-definition streaming. With AES-256 encryption, double encryption, and a no-logs policy, NordVPN prioritizes user privacy. It also supports Netflix, Hulu, and Amazon Prime Video, making it a versatile choice for content lovers. ExpressVPN – Speed and Simultaneous Connections ExpressVPN is another leading provider in the best vpn for streaming services market. Known for its fast speeds and zero lag, it’s ideal for buffer-free streaming. The service supports up to 5 devices at once, which is perfect for households. ExpressVPN also unblocks popular platforms like Disney+, HBO Max, and Sony Liv, making it a top pick for those seeking global content. Surfshark – Affordable and Feature-Rich For budget-conscious users, Surfshark is a strong contender in the best vpn for streaming services category. It offers unlimited bandwidth, fast speeds, and a no-logs policy. With over 3,000 servers in 100+ countries, Surfshark can unlock regional content on Netflix, Amazon Prime Video, and other platforms. Its affordable pricing and user-friendly interface make it a great option for newcomers. CyberGhost – Easy to Use with Strong Streaming Support CyberGhost is a user-friendly VPN that’s ideal for beginners. It’s often recommended as one of the best vpn for streaming services due to its streaming-specific servers and easy setup process. The service supports Netflix, Hulu, and YouTube, and its no-logs policy ensures data privacy. CyberGhost also offers fast speeds and uninterrupted streaming, making it a solid choice for those who prioritize ease of use. Private Internet Access (PIA) – Affordable and Secure Private Internet Access is a budget-friendly option for streaming enthusiasts. It provides strong security features, fast speeds, and unlimited bandwidth. While PIA may not have as many servers as some competitors, it still supports popular streaming platforms like Netflix and Amazon Prime Video. Its simple interface and affordable plans make it a top contender for those looking for value. Comparative Analysis: Which Is the Best VPN for Streaming Services? Speed and Performance When it comes to streaming services, speed is critical. The best vpn for streaming services should maintain high speeds even when accessing geo-restricted content. NordVPN and ExpressVPN are leaders in this category, offering fast connections and low latency. Surfshark and CyberGhost also perform well, but PIA may lag slightly in speed for some users. Security and Privacy Features Security is a key factor when choosing the best vpn for streaming services. NordVPN and ExpressVPN stand out with AES-256 encryption, strong privacy policies, and no-logs commitments. Surfshark and CyberGhost also offer similar security features, but PIA provides additional benefits like multi-hop connections and strong encryption protocols. Server Locations and Global Coverage Server locations determine how well a VPN can unlock regional content. The best vpn for streaming services should have servers in multiple countries, including the US, UK, and Japan, to support global content libraries. NordVPN and ExpressVPN lead in this area, with servers in over 100 countries, while PIA has fewer server locations but still covers major regions. Compatibility and App Support Compatibility with streaming platforms is essential for the best vpn for streaming services. NordVPN,
How to Use a VPN for Secure Internet: A Step-by-Step Guide
How to use vpn for secure internet is an essential skill for anyone concerned about online privacy and security. In today’s hyper-connected world, where cyber threats are increasingly sophisticated, securing your internet connection has become a top priority. A VPN (Virtual Private Network) is a powerful tool that encrypts your data, hides your IP address, and ensures your online activities remain private. Whether you’re a casual internet user or a business professional, understanding how to use a VPN for secure internet can protect you from hackers, surveillance, and data breaches. This article will guide you through the process of selecting, setting up, and using a VPN for secure internet effectively. We’ll break down the steps in detail, so you can confidently enhance your digital security without any technical hassle. Understanding the Basics of a VPN Before diving into the step-by-step guide, it’s crucial to grasp the fundamentals of what a VPN for secure internet is and how it works. A VPN is a service that creates a secure and encrypted connection over a less secure network, such as the public internet. It acts as a digital tunnel, protecting your data from being intercepted by malicious actors. What is a VPN? A VPN for secure internet is a technology that allows users to create a private network connection through a public internet infrastructure. It works by routing your device’s internet traffic through a server operated by the VPN provider, masking your IP address and encrypting your data. This makes it difficult for anyone to track your online activities or access your sensitive information. How a VPN Secures Your Internet Connection When you connect to a VPN for secure internet, your data is encrypted using advanced protocols like AES-256 or OpenVPN. This encryption ensures that even if someone intercepts your data, they can’t decipher it without the encryption key. Additionally, a VPN assigns you a new IP address, making it appear as though you’re browsing from a different location. This not only hides your real identity but also helps bypass geographical restrictions and censorship. The Importance of Secure Internet In an era where cyberattacks are rampant, a secure internet connection is vital for protecting your personal and financial data. A VPN for secure internet provides an extra layer of security by shielding your online activities from prying eyes. It’s particularly useful for users who frequently access public Wi-Fi networks, as these are common targets for hackers looking to steal sensitive information. Choosing the Right VPN for Your Needs Selecting the best VPN for secure internet depends on your specific requirements, budget, and the level of protection you need. With so many providers available, it’s essential to evaluate them based on key factors like security, speed, user-friendliness, and pricing. Factors to Consider When Choosing a VPN When evaluating a VPN for secure internet, there are several important aspects to keep in mind: – Security Protocols: Look for strong encryption standards like AES-256 and secure protocols such as OpenVPN or WireGuard. – Server Locations: A larger number of servers means better performance and more options for bypassing geo-restrictions. – Speed and Bandwidth: Choose a provider that offers fast connections and unlimited data usage. – Price and Plans: Compare monthly and annual subscription options to find the best value. – Additional Features: Consider features like kill switch, split tunneling, and multi-device support. A secure internet connection also requires a reliable provider with a strict no-logs policy. This ensures that your online activities are not stored or shared with third parties. Additionally, check if the VPN for secure internet has a good reputation for customer support and compatibility with different devices and operating systems. Types of VPN Services There are several types of VPN services available, each tailored to different needs: – Consumer VPNs: Designed for everyday users, these are typically easy to set up and offer basic security features. – Business VPNs: Ideal for companies, these provide advanced security options, such as multi-factor authentication and enterprise-grade encryption. – Mobile VPNs: Optimized for smartphones and tablets, they ensure secure browsing on the go. – Free vs. Paid VPNs: While free options are tempting, they often come with limitations like data caps, slower speeds, and fewer servers. When choosing a VPN for secure internet, consider your usage patterns. For example, if you’re a student who needs access to educational resources, a provider with a strong no-logs policy and good server coverage is ideal. On the other hand, businesses might prioritize enterprise features and 24/7 customer support. Reputable VPN Providers Some of the most trusted VPN for secure internet providers include ExpressVPN, NordVPN, Surfshark, and ProtonVPN. Each offers unique benefits: – ExpressVPN: Known for its fast speed and strong security, it’s a popular choice for users who prioritize performance. – NordVPN: Offers extra security features like double encryption and a no-logs policy, making it ideal for privacy-conscious users. – Surfshark: A budget-friendly option that provides unlimited devices and good server coverage. – ProtonVPN: Backed by the CERN, it’s a secure internet provider that focuses on privacy and encryption. Before making a decision, read reviews and check for any security vulnerabilities or data leaks reported by users. A reliable VPN for secure internet should have a proven track record of protecting user data and maintaining privacy. Step-by-Step Guide to Setting Up a VPN Setting up a VPN for secure internet is a straightforward process, but it requires attention to detail to ensure optimal security and performance. Follow these steps to get started. Research and Select a Reliable Provider The first step in How to use vpn for secure internet is to choose a secure internet provider that fits your needs. Start by researching free vs. paid VPNs and comparing their features. Look for a provider with strong encryption, a no-logs policy, and good server locations. Additionally, check if the provider offers split tunneling or multi-device support. Once you’ve narrowed down your options, consider the user interface and customer support. A user-friendly interface makes it easier to configure the
Secure VPN for Corporate Use: Reliable and Secure Connectivity
In today’s digital landscape, secure vpn for corporate use has become essential for businesses aiming to protect sensitive data and ensure seamless communication across remote teams and distributed networks. As companies increasingly rely on cloud computing, online collaboration tools, and digital workflows, the need for robust, encrypted connectivity has never been higher. A Secure VPN not only safeguards data in transit but also serves as a critical component of an organization’s cybersecurity strategy, enabling secure access to internal resources while maintaining performance and scalability. From small startups to large enterprises, implementing a reliable secure vpn for corporate use can significantly reduce the risk of cyberattacks, data breaches, and unauthorized access. This article explores the importance of Secure VPNs, their key features, types, best practices, and real-world applications to help businesses choose and optimize the right solution for their needs. The Importance of Secure Corporate VPNs In an era where cyber threats are constantly evolving, secure vpn for corporate use plays a vital role in protecting an organization’s digital assets. A Virtual Private Network (VPN) creates a secure tunnel between a user’s device and the company’s network, ensuring that data transmitted over public internet remains encrypted and private. This is especially crucial for remote employees, who often access company systems from unsecured locations such as coffee shops, airports, or home offices. Without a Secure VPN, sensitive information like client data, financial records, and internal communications is vulnerable to interception by malicious actors. One of the primary reasons businesses invest in secure vpn for corporate use is to maintain data integrity and confidentiality. By encrypting all traffic, a Secure VPN prevents unauthorized access to files, emails, and applications. This is particularly important for industries such as healthcare, finance, and legal services, where data privacy regulations like GDPR, HIPAA, and SOX require strict security measures. In addition to encryption, Secure VPNs also provide multi-factor authentication (MFA), adding an extra layer of protection against credential-based attacks. Another significant benefit of Secure VPNs is their ability to support remote access and secure file sharing. With the rise of hybrid and remote work models, employees need to connect to company servers and networks from anywhere in the world. A Secure VPN ensures that these connections are secure, allowing users to access internal resources as if they were on the company’s local network. This flexibility is essential for modern businesses that prioritize productivity and agility. Furthermore, Secure VPNs enable seamless integration with cloud-based infrastructure, allowing organizations to leverage remote servers while maintaining control over data flow and access. Data Security and Protection Data security is a cornerstone of any effective secure vpn for corporate use strategy. Businesses store vast amounts of sensitive information, including customer records, trade secrets, and internal communications. A Secure VPN ensures that this data is protected from eavesdropping, man-in-the-middle attacks, and data leakage by encrypting all network traffic. This encryption is typically achieved through advanced protocols like AES-256 or RSA-4096, which scramble data into an unreadable format for unauthorized users. The use of end-to-end encryption (E2EE) in Secure VPNs adds another layer of protection, ensuring that data is encrypted both during transmission and while stored on remote servers. This is particularly important for secure file sharing across teams, as it prevents any third-party from accessing or modifying files without proper authorization. In addition to encryption, Secure VPNs often include data integrity checks and firewall integration, which help detect and block suspicious activities in real time. These features are critical for corporate data protection, especially when dealing with large-scale data transfers or sensitive transactions. Remote Access and Flexibility Secure corporate VPNs are designed to facilitate secure remote access without compromising the integrity of the company’s network. Unlike traditional internet connections, a Secure VPN creates a private, encrypted tunnel that allows users to access internal systems as if they were physically present on the company premises. This secure remote access capability is indispensable for businesses with distributed teams, as it ensures consistent performance and reliability across different locations. Moreover, Secure VPNs support mobile workforce connectivity, enabling employees to work from anywhere while maintaining the same level of security as if they were in the office. This is especially relevant for industries like telecommunications, IT services, and consulting, where professionals often travel between clients and need immediate access to company resources. The flexibility of a Secure VPN also extends to remote file sharing, allowing teams to collaborate on documents, databases, and applications without exposing them to external threats. A Secure VPN can be integrated with existing IT infrastructure, such as cloud storage platforms, enterprise applications, and mobile devices, ensuring that all data flows through a secure channel. This seamless integration reduces the risk of data breaches and unauthorized access, making it easier for businesses to scale their operations while maintaining a high level of security. Compliance and Regulatory Adherence For businesses operating in highly regulated industries, secure vpn for corporate use is not just a convenience—it’s a necessity. Compliance with data protection standards like GDPR, HIPAA, and SOX requires organizations to implement strict data security protocols and access controls. A Secure VPN ensures that these requirements are met by providing encrypted data transmission, user authentication, and audit trails that document access and activity within the network. Regulatory frameworks often mandate secure data storage and secure data transmission, which a Secure VPN addresses by creating a private network environment. This environment is essential for compliance audits, as it simplifies the tracking of user activities and data movements. In addition, Secure VPNs help businesses avoid legal penalties by ensuring that sensitive information is protected from third-party breaches and data leaks. Moreover, secure vpn for corporate use can be tailored to meet the specific regulatory requirements of different industries. For example, financial institutions may prioritize AES-256 encryption, while healthcare providers might focus on HIPAA-compliant features. By selecting the right Secure VPN solution, companies can ensure long-term compliance while adapting to evolving security standards. Key Features to Look for in Secure Corporate VPNs When selecting a secure vpn for
How to Use a VPN for Remote Desktop: A Complete Guide
In today’s digital age, remote work has become a necessity for many professionals. Whether you’re connecting to a company network, accessing sensitive data, or working from different locations, using a vpn for remote desktop can significantly enhance your security, privacy, and overall productivity. This article will guide you through the process of setting up and utilizing a virtual private network (VPN) for remote desktop access, covering everything from the basics to advanced tips for long-term efficiency. Why Use a VPN for Remote Desktop? Remote desktop access allows users to connect to their computers or servers from anywhere in the world. However, without proper security measures, this method can expose your data to potential threats. A vpn for remote desktop creates a secure and encrypted tunnel between your device and the network, protecting your connection from hackers, unauthorized access, and data breaches. One of the primary reasons to use a VPN for remote desktop is to ensure secure remote access. When you connect to a remote desktop, your data travels over public networks, which can be vulnerable to interception. A VPN encrypts this data, making it much harder for cybercriminals to access. Additionally, using a vpn for remote desktop allows you to bypass geographical restrictions, enabling access to resources located in different regions. Another key benefit is anonymity and privacy. By routing your internet traffic through a remote server, a vpn for remote desktop hides your real IP address, making it more difficult for websites or third parties to track your online activities. This is especially important if you’re working with confidential information or using public Wi-Fi networks. Getting Started: Choosing the Right VPN Before you can use a vpn for remote desktop, you need to select the right service. There are several factors to consider, including security protocols, server locations, speed, and user-friendliness. Understanding the Basics of a Remote Desktop Connection A remote desktop connection allows you to access your computer from another device, such as a laptop or smartphone. This is particularly useful for IT professionals, remote workers, or anyone who needs to control their machine from a different location. When using a vpn for remote desktop, the connection is secured through encryption, ensuring that your data remains private. To set up a remote desktop connection, you need to have the remote desktop protocol (RDP) enabled on your target machine. This is commonly used in Windows systems, but other platforms like macOS or Linux also offer similar functionality. Once RDP is configured, you can connect using a client application or a web-based interface. Selecting a Reliable VPN Provider Not all VPNs are created equal. When choosing a vpn for remote desktop, look for providers that offer strong encryption, a no-logs policy, and a good number of server locations. OpenVPN, IKEv2, and WireGuard are popular protocols known for their security and performance. OpenVPN is a widely used protocol that offers a balance between security and speed. It supports both TCP and UDP, making it versatile for different network conditions. IKEv2 is another option, known for its fast reconnection and stability, especially on mobile devices. WireGuard, on the other hand, is newer and more efficient, providing high-speed connections with strong security. Comparing Key Features of Different VPNs <table style="border-collapse: collapse; width: 100%; margin: 20px 0;"> Feature OpenVPN IKEv2 WireGuard Security Strong, supports AES-256 Secure, with IPsec and AES-256 High, with ChaCha20 and BLAKE2 Speed Moderate to high Fast, especially on mobile Very fast, optimized for performance Compatibility Widely compatible Good on Windows and macOS Supports multiple platforms Encryption SSL/TLS and strong cipher options IPsec, strong encryption Efficient encryption Logs Many providers offer no-logs Some providers have no-logs No-logs policies available When selecting a vpn for remote desktop, it’s crucial to evaluate these features based on your specific needs. If speed is a priority, WireGuard might be the best choice. For maximum security, OpenVPN or IKEv2 could be more suitable. Setting Up Your VPN for Remote Desktop Access Once you’ve chosen a vpn for remote desktop, the next step is to set it up on your device. This process may vary slightly depending on your operating system and the VPN service you select. Installing the VPN Software Most vpn for remote desktop services require you to install their client software on your device. This is typically a simple process, involving downloading the application from the provider’s website and following the installation prompts. Once installed, you can open the app and enter your login credentials to connect. Some providers offer mobile apps, making it easy to access your remote desktop from your smartphone or tablet. For desktop users, the software is usually compatible with Windows, macOS, and Linux. It’s important to ensure that the vpn for remote desktop software is updated to the latest version to avoid security vulnerabilities. Configuring the Remote Desktop Connection After setting up the vpn for remote desktop, you need to configure your remote desktop connection. This involves selecting the correct protocol (e.g., RDP, VNC, or SSH) and ensuring that the necessary ports are open on your target machine. If you’re using a vpn for remote desktop with a remote server, you may need to enter the server’s IP address or domain name. Some services allow you to connect to a remote desktop through a web portal, while others require a dedicated client application. Once everything is configured, you can test the connection to ensure it works as expected. Testing and Verifying the Connection Before relying on your vpn for remote desktop for daily work, it’s essential to test the connection thoroughly. This includes checking for encryption, confirming that your IP address is hidden, and ensuring that your remote desktop session is stable and fast. You can also verify the connection by accessing internal resources that are typically restricted to the company network. If you can successfully connect to these resources through the vpn for remote desktop, then the setup is likely correct. Additionally, monitoring your data usage and connection speed can help identify any issues that may
What New Reports Say About Free VPN Security Risks
In recent months, new reports on free VPN security risks have sparked significant debate among cybersecurity experts, tech enthusiasts, and everyday internet users. These studies highlight growing concerns about the safety of free virtual private network (VPN) services, which have become increasingly popular due to their affordability and ease of use. While free VPNs offer a convenient way to enhance online privacy and bypass geographical restrictions, they are not without vulnerabilities. From data leaks to hidden tracking mechanisms, the reports reveal that many free providers may compromise user security in ways that are not immediately obvious. This article delves into the findings of these latest studies, explores the key security risks associated with free VPNs, and provides actionable insights for users seeking to protect their digital footprint. The Rise of Free VPNs and Their Appeal Free VPNs have gained immense popularity in the digital age, driven by their accessibility and cost-effectiveness. For users who are budget-conscious or new to cybersecurity, these services provide a simple way to secure their internet connections without requiring a subscription. Many free VPNs are promoted as tools to protect privacy, encrypt data, and access content from other regions. However, their free model often comes with trade-offs. Unlike paid services, which typically offer dedicated servers, advanced encryption protocols, and customer support, free VPNs may rely on advertising, data monetization, or limited resources to sustain their operations. The convenience of free VPNs is undeniable. They are easy to install, often available on mobile devices and desktops, and require minimal setup. This low barrier to entry has made them a go-to solution for people who need occasional privacy protection. Yet, the growing number of users has also attracted the attention of cybersecurity researchers, who have uncovered alarming patterns in how these services handle user data. The new reports on free VPN security risks emphasize that while free VPNs can be useful in certain scenarios, they often pose a higher risk of data exposure compared to their paid counterparts. The popularity of free VPNs has also created a competitive market, with many providers vying for users’ attention through aggressive marketing. This has led to the proliferation of free services that promise robust security but may lack the necessary infrastructure to deliver it. As a result, users must be cautious about which free VPNs they choose, as the new reports on free VPN security risks suggest that not all providers are created equal. Key Security Risks Exposed by the Latest Studies The new reports on free VPN security risks have identified several critical vulnerabilities in free virtual private network (VPN) services. One of the most pressing issues is the potential for data leaks, where user information such as IP addresses, browsing history, and even personal details are shared with third parties. These leaks can expose users to targeted advertising, surveillance, and even identity theft. Another major concern is the lack of transparent data policies, which often make it difficult for users to understand how their data is being used or sold. A significant finding from the reports is the presence of logging practices in many free VPNs. While some services claim to be “no-log” providers, the studies reveal that certain free platforms may still retain logs of user activity for analytical or commercial purposes. These logs can include timestamps, website visits, and connection durations, which can be valuable to hackers or advertisers. Additionally, the reports highlight that free VPNs often use shared servers, which can lead to slower speeds and a higher risk of data interception. When multiple users share the same server, it becomes easier for one user’s data to be accessed by others, especially if the server is not properly secured. Another risk mentioned in the new reports on free VPN security risks is the limited encryption standards used by some free providers. While many free VPNs claim to use AES-256 encryption, the studies indicate that some may employ weaker protocols, leaving users’ data more susceptible to breaches. This is particularly concerning for users who rely on free VPNs to protect sensitive information, such as financial transactions or personal communications. Understanding the Scope of Free VPN Security Risks The new reports on free VPN security risks have analyzed a wide range of free services, identifying patterns in their security practices. These studies often compare free and paid options, revealing that while paid services may have more resources to invest in security, free providers are not without merit. However, the trade-offs between cost and security are becoming more apparent. One of the key aspects examined in the reports is the data collection practices of free VPNs. Many of these services collect user data as a means of generating revenue. This includes information like browsing habits, location data, and even the amount of data transferred. The reports note that some providers may sell this data to third-party advertisers, which can lead to targeted marketing and potential privacy violations. Users who are unaware of these practices may unknowingly compromise their online anonymity. The studies also emphasize the importance of trust in free VPNs. Since many of these services operate with minimal transparency, users must scrutinize their privacy policies and user reviews before relying on them. The new reports on free VPN security risks suggest that even a single data breach can have long-lasting consequences for users who have entrusted their information to a free provider. The Hidden Costs of Free VPNs Data Monetization and Advertising Free VPNs often monetize user data by integrating advertisements into their platforms. These ads can range from simple banners to more intrusive pop-ups or even embedded tracking scripts. The new reports on free VPN security risks highlight that some providers use ad-supported models to generate revenue, which may slow down the browsing experience or expose users to targeted marketing. While ads are a common feature, the reports warn that they can also be a vector for data collection. For example, some free VPNs include third-party tracking tools that monitor user behavior across different websites. This
Breaking Down Remote Access Security: How It Works
In today’s digital age, remote access security has become a critical component of modern business operations. With the rise of remote work, cloud computing, and digital transformation, organizations rely heavily on secure remote access to ensure productivity, collaboration, and data integrity. The question how does remote access security work is at the heart of understanding this essential process. Remote access security involves the use of technologies, protocols, and strategies to protect sensitive data, systems, and networks from unauthorized access, cyber threats, and potential breaches. This article will delve into the mechanics of remote access security, breaking down its core components, technologies, and best practices to help you grasp its significance in today’s interconnected world. Understanding the Fundamentals of Remote Access Security Remote access security is the practice of enabling users to connect to a network, system, or application from a distant location while maintaining the confidentiality, integrity, and availability of data. This process is vital for businesses that operate globally, allowing employees, partners, and clients to access resources without being physically present. However, with the increasing use of remote access, the risk of cyberattacks also grows. Hackers can exploit vulnerabilities in remote access protocols to gain unauthorized entry, steal sensitive information, or disrupt operations. The primary goal of remote access security is to authenticate users, authorize their access, and encrypt data during transmission. This ensures that only trusted individuals can access critical systems, and that their data remains secure even when transmitted over public networks. To achieve this, organizations implement a combination of authentication methods, encryption protocols, and access control policies. These measures work together to create a layered defense system, reducing the likelihood of successful attacks. One of the most common ways remote access security is implemented is through virtual private networks (VPNs). A VPN creates an encrypted tunnel between a user’s device and the organization’s network, protecting data from prying eyes. However, remote access security isn’t limited to VPNs. There are other technologies like secure shell (SSH), remote desktop protocols (RDP), and multi-factor authentication (MFA) that also play a crucial role in safeguarding digital assets. These tools are designed to mitigate risks associated with remote connections, ensuring that only authorized users can access systems and data. Core Components of Remote Access Security Authentication and Authorization Authentication is the process of verifying a user’s identity before granting access to a system or network. This is typically done through multi-factor authentication (MFA), which requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device. MFA significantly reduces the risk of unauthorized access by adding an extra layer of security. Authorization follows authentication, determining what level of access a user is allowed to have. This is managed through role-based access control (RBAC), where permissions are assigned based on the user’s role within an organization. For example, a junior employee might have access to specific files, while a manager can access broader data sets. This method ensures that users can only access the resources necessary for their work, minimizing the potential damage of a breach. In addition to MFA and RBAC, biometric authentication (such as fingerprint or facial recognition) is becoming more prevalent in high-security environments. These methods are more difficult to replicate than traditional passwords, making them a powerful tool in the fight against identity theft. However, they also require robust infrastructure and can be more complex to implement. Encryption and Data Protection Data encryption is a fundamental aspect of remote access security. When data is transmitted over a network, it is often encrypted to prevent interception by malicious actors. Transport Layer Security (TLS) and Secure Sockets Layer (SSL) are two of the most widely used encryption protocols that ensure data remains private and secure during transit. Encryption works by converting readable data into an unreadable format using cryptographic algorithms. This process is essential for protecting sensitive information such as login credentials, financial data, and personal records. Without encryption, data sent over public networks like the internet is vulnerable to man-in-the-middle attacks, where attackers intercept and alter information in real-time. There are two main types of encryption: symmetric and asymmetric. Symmetric encryption uses a single key for both encryption and decryption, making it faster but potentially less secure if the key is compromised. Asymmetric encryption, on the other hand, uses a public and private key pair, offering stronger security. Modern remote access systems often employ a combination of both methods to balance speed and security. Network Access Control (NAC) Network Access Control (NAC) is another key component of remote access security. NAC ensures that only authorized devices and users can connect to a network. It works by evaluating the security posture of a device before granting access, checking for factors such as up-to-date software, firewall settings, and antivirus status. This technology is particularly useful in environments where multiple users and devices access the same network. NAC can automatically enforce security policies, such as requiring software updates or patch management, to reduce the risk of vulnerabilities. It also allows for dynamic access control, where permissions are adjusted in real-time based on user behavior and device status. By integrating NAC with other security measures like MFA and encryption, organizations can create a comprehensive defense against threats. This approach not only secures data in transit but also prevents unauthorized devices from accessing the network, thereby protecting the entire system from potential breaches. Types of Remote Access Technologies Virtual Private Networks (VPNs) VPNs are one of the most common remote access technologies used today. They create an encrypted connection between a user’s device and the organization’s network, ensuring that data is protected even when transmitted over public internet connections. A key advantage of VPNs is their ability to provide secure access to internal resources, such as servers, databases, and employee workstations. They also allow users to access the internet through a remote server, masking their IP address and location. However, VPNs can be vulnerable to split tunneling, where some traffic bypasses the encrypted tunnel,
Ohio State vs Purdue College Football Preview
As the college football season kicks off, fans across the nation are eagerly anticipating a slate of highly anticipated matchups that promise thrilling action and competitive battles. Among these, Ohio State vs Purdue, Georgia vs MS State, and BYU vs Texas Tech stand out as key games that could set the tone for the upcoming campaign. Each of these matchups brings together teams with contrasting styles, histories, and ambitions, making them perfect examples of how diverse college football can be. Whether it’s the storied rivalry between Ohio State and Purdue, the explosive talent of Georgia and MS State, or the underdog narrative of BYU versus Texas Tech, these games are more than just matches—they’re cultural events that reflect the heart and passion of the sport. This preview delves into the intricacies of each game, offering insights into their historical context, current team strengths, and what fans can expect from these matchups. Ohio State vs Purdue Historical Context The Ohio State vs Purdue rivalry is one of the oldest and most storied in college football, with roots dating back to 1897. Over the years, this matchup has produced iconic moments, from the legendary “Buckeye Bowl” games to the epic 2007 clash that saw Ohio State dominate 52-16. The rivalry has been a proving ground for many legendary players, including Johnny Lujack and Archie Griffin, who defined the era of Ohio State football in the 1970s. Purdue, on the other hand, has a history of producing gritty underdogs, often competing fiercely despite being the underdog in many matchups. This dynamic has created a compelling narrative, with each game bringing a blend of tradition and tension. The Buckeyes and Boilermakers have faced off 101 times as of 2023, with Ohio State holding a commanding 67-34 record. However, the recent years have seen a shift in the balance of power, with Purdue challenging Ohio State more frequently. For example, in the 2019 season, Purdue shocked the nation by defeating Ohio State 45-44 in a thrilling overtime game. This rivalry is not just about the scoreline—it’s about the history, the passion of fans, and the legacy of each program. Current Season Analysis In the 2024 season, both Ohio State and Purdue are entering the matchup with different goals and challenges. The Buckeyes, led by head coach Ryan Day, are expected to be one of the top teams in the Big Ten, with a roster filled with elite talent. Ohio State’s offense, powered by quarterback C.J. Stroud and a deep receiving corps, has the potential to dominate, while their defense, anchored by defensive end De’Von freshman, will be tested by Purdue’s physical style. On the other hand, Purdue is looking to build on their recent successes. Head coach Jeff Brohm has transformed the program into a consistent contender, emphasizing a balanced approach that blends athleticism with strategy. The Boilermakers have shown improved consistency in recent years, with their defense becoming a more reliable force. However, their offense, while talented, has faced some challenges in maintaining a high level of performance throughout the season. The matchup is set for early September, and the location will play a crucial role in determining the outcome. The game will be played at Lucas Oil Stadium in Indianapolis, a neutral site that adds an extra layer of intensity. With both teams having different strengths, this game is poised to be a classic. Key Players and Roles The Buckeyes will rely heavily on their offensive firepower, with C.J. Stroud expected to shine as the team’s quarterback. Stroud’s ability to throw deep passes and manage the game will be critical, especially if Ohio State’s defense struggles early. The offensive line, led by standout players like Rashod George and Chase Brown, will also play a pivotal role in creating opportunities for the running game. For Purdue, the key to success lies in their ability to control the tempo and exploit Ohio State’s defense. Running back Jalek Marshall has emerged as a potential breakout star, and his performance could determine the outcome of the game. The Boilermakers also have a strong defensive line, with players like Tyrone Nix and Terrence Nunn, who could put pressure on Stroud and disrupt Ohio State’s offensive rhythm. Team Strengths and Weaknesses Ohio State’s strengths lie in their offensive talent and experience. The team has a deep roster with multiple high-level athletes, and their coaching staff has a proven track record of developing players. However, weaknesses include their defense’s ability to contain Purdue’s dynamic offense, particularly if the Boilermakers manage to establish a strong running game. Purdue’s strengths are their athleticism and resilience. The team has shown the ability to compete with powerhouse programs, and their defense is more organized than in previous seasons. Their weaknesses, however, include occasional inconsistencies in the offense, which may struggle to keep up with Ohio State’s high-octane attack. Game Strategy and Expectations Ohio State is likely to focus on a fast-paced, high-scoring offense to overwhelm Purdue’s defense. The Buckeyes will need to maintain their rhythm and avoid turnovers, as their defense may be tested by Purdue’s physical style. Purdue, on the other hand, may adopt a balanced strategy, using their running game to set the tone and then exploiting Ohio State’s vulnerabilities with explosive plays. The Boilermakers will also look to capitalize on their home-field advantage, with the electric atmosphere at Lucas Oil Stadium providing a boost. Georgia vs MS State Rivalry Background The Georgia vs MS State matchup has become a regular feature in the SEC schedule, with both teams vying for dominance in the South division. While Georgia has a storied history and a reputation as a powerhouse, MS State has emerged as a formidable challenger, especially in recent years. The rivalry is often seen as a test of grit and determination, with MS State’s underdog spirit contrasting against Georgia’s elite status. Georgia’s historical dominance over MS State is evident, with a 25-4 record in the series as of 2023. However, the 2021 game, where MS State upset Georgia 38-35 in
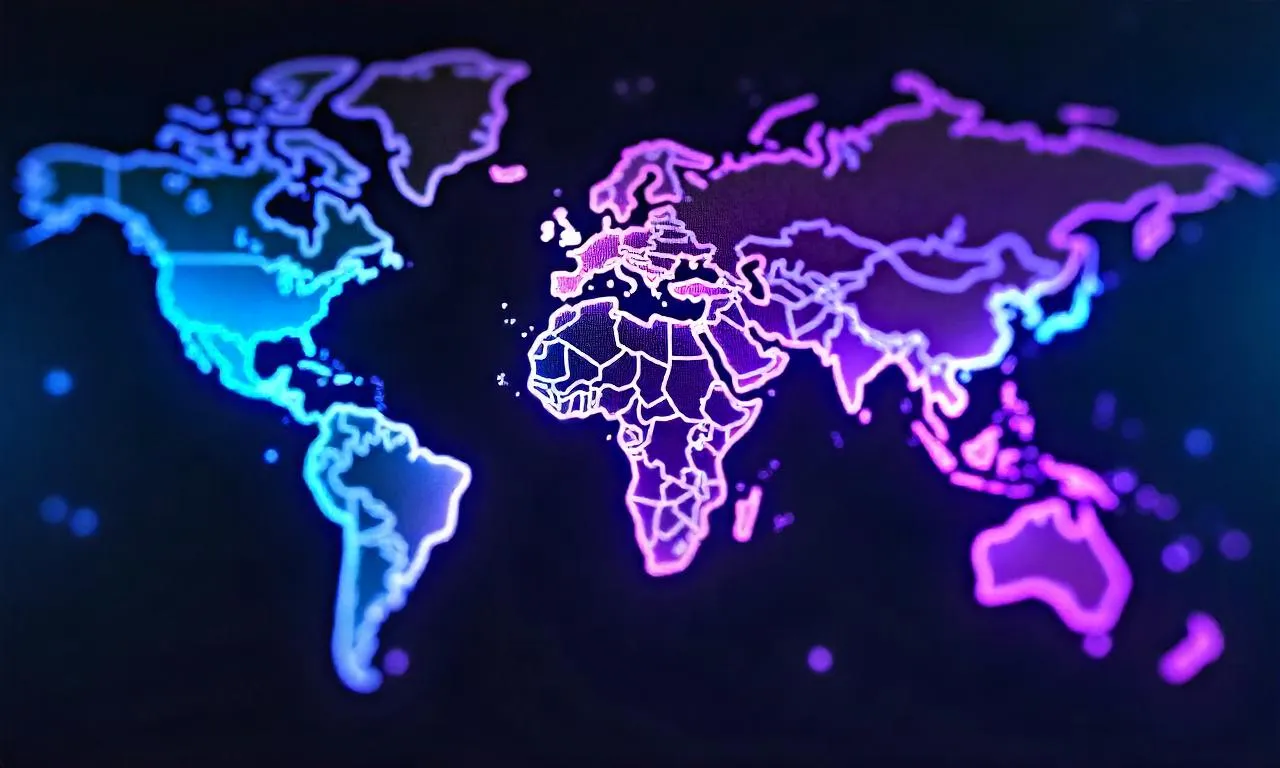
Understanding VPN Usage Statistics in Different Regions
In today’s digital age, Virtual Private Networks (VPNs) have become essential tools for securing online privacy, bypassing internet censorship, and accessing geo-restricted content. As the demand for secure browsing and data protection continues to rise, understanding vpn usage statistics in different regions is crucial for businesses, policymakers, and users alike. These statistics not only reveal how widespread VPN adoption is but also highlight the unique factors driving its growth in specific areas. From North America’s tech-driven culture to Asia-Pacific’s rapid internet expansion, each region presents a distinct picture of how people interact with virtual private networks. This article explores these regional variations in depth, offering insights into the trends, challenges, and opportunities shaping the global VPN landscape. Global Trends in VPN Adoption The Rise of Digital Privacy Awareness The surge in vpn usage statistics in different regions is closely tied to growing digital privacy concerns. With more people accessing sensitive information online, such as financial data, health records, and personal communications, the need for encrypted connections has become paramount. This trend is evident across all continents, but the extent of adoption varies significantly depending on local regulations, cultural attitudes toward privacy, and the availability of internet services. For instance, countries with stringent data protection laws often see higher VPN usage rates, as citizens are more aware of their rights to secure online data. Technological Advancements and User Demands The evolution of vpn usage statistics in different regions is also influenced by technological advancements. As internet speeds improve and devices become more connected, users seek greater control over their online activities. This includes bypassing content restrictions, accessing streaming platforms, and protecting against cyber threats. The rise of remote work and online learning further fueled the need for secure connections, especially in regions with high internet penetration. Additionally, the proliferation of mobile devices has made vpn usage statistics in different regions more accessible, allowing users to secure their data on the go. Regional Differences in Internet Accessibility Internet accessibility plays a key role in shaping vpn usage statistics in different regions. In regions where internet infrastructure is well-developed, such as North America and Western Europe, users are more likely to adopt vpn usage statistics in different regions for enhanced security. Conversely, in areas with limited connectivity or high censorship, such as certain parts of Asia and Africa, vpn usage statistics in different regions often spike due to the need for bypassing content restrictions. This dynamic underscores the importance of analyzing regional data to understand the underlying drivers of vpn usage statistics in different regions. The Impact of Cybersecurity Threats Cybersecurity threats have emerged as a significant factor influencing vpn usage statistics in different regions. Regions prone to data breaches, hacking attempts, or surveillance often experience higher adoption rates. For example, vpn usage statistics in different regions in countries with frequent cyberattacks or political monitoring are typically higher than in more stable regions. This highlights how vpn usage statistics in different regions are not only a reflection of technological trends but also a response to real-world security challenges. The Role of Government Policies Government policies in various regions have a profound impact on vpn usage statistics in different regions. While some countries actively promote the use of vpn usage statistics in different regions for national security or to monitor internet activity, others have enacted laws that make it easier for citizens to use them. This duality is evident in the contrasting approaches to vpn usage statistics in different regions in regions like the European Union, where privacy regulations encourage widespread use, and countries like China, where vpn usage statistics in different regions are often driven by the need to access censored content. North America: Tech-Savvy and Privacy-Driven The Digital Natives of North America North America, particularly the United States and Canada, leads the way in vpn usage statistics in different regions due to its tech-savvy population and strong emphasis on digital privacy. The region’s users are often early adopters of new technologies, which makes them more inclined to use vpn usage statistics in different regions for securing their online activities. This is especially true in the U.S., where concerns about data collection by tech giants and government agencies have fueled the demand for encrypted connections. High Adoption Rates and Market Growth According to recent studies, vpn usage statistics in different regions in North America hover around 45-50%, with the U.S. alone accounting for a significant portion of the global market. This high adoption rate is driven by several factors, including the availability of high-speed internet, a strong cybersecurity culture, and the influence of media on privacy issues. Moreover, the region’s competitive VPN market, with numerous providers offering tailored services, has made it easier for users to access and adopt vpn usage statistics in different regions. Emerging Trends in the Region As the demand for secure browsing continues to grow, vpn usage statistics in different regions in North America are evolving. One notable trend is the rise of zero-knowledge proof (ZKP) and end-to-end encryption (E2EE) technologies, which are becoming more popular among users seeking maximum privacy. Additionally, the integration of vpn usage statistics in different regions with smart home devices and IoT (Internet of Things) systems is gaining traction, reflecting the region’s innovative approach to digital security. The Influence of Remote Work The shift to remote work during the pandemic accelerated the adoption of vpn usage statistics in different regions in North America. Businesses began prioritizing secure data transmission, leading to increased use of vpn usage statistics in different regions in both corporate and personal settings. This trend is expected to continue as hybrid work models become the norm, further solidifying vpn usage statistics in different regions as a staple of modern digital life. The Role of Education and Awareness Cybersecurity Education in Schools One of the key reasons for vpn usage statistics in different regions in North America is the robust cybersecurity education system. Schools and universities in the region often incorporate digital privacy lessons into their curricula, ensuring that students are
Failed, contact support
In today’s digital age, remote desktop connections have become essential for productivity, enabling users to access their workstations from anywhere. However, how to secure a remote desktop connection is a critical skill that every user must master to protect sensitive data and prevent cyberattacks. A failed remote desktop connection can be frustrating, but it often signals a deeper issue—like unsecured access, outdated software, or weak authentication protocols. Whether you’re a business professional managing remote servers or a student accessing virtual labs, ensuring a secure remote desktop setup is not just about convenience, but also about safeguarding your digital assets. This article will guide you through how to secure a remote desktop connection using the latest SEO best practices and actionable strategies. We’ll explore key vulnerabilities, practical steps to enhance security, and tools that can help you maintain a safe and reliable remote access environment. By the end of this guide, you’ll have a clear understanding of how to prevent failures, troubleshoot issues, and keep your remote desktop experience secure for years to come. Understanding Remote Desktop Security Remote desktop security is the foundation of any reliable remote access setup. It involves implementing measures to protect the connection from unauthorized access, data breaches, and network threats. A secure remote desktop setup ensures that only authenticated users can access the system, and all data transmitted remains encrypted. Without proper security, a remote desktop connection can be exploited by malicious actors, leading to data loss, system downtime, or even ransomware attacks. One of the primary goals of remote desktop security is to minimize the risk of unintended vulnerabilities. For instance, if a user’s password is weak or their software is outdated, attackers can easily compromise the connection. Additionally, using a public Wi-Fi network without proper encryption can expose your data to eavesdropping. Therefore, understanding the security landscape is the first step in building a robust remote access strategy. The Role of Encryption in Remote Desktop Security Encryption is a vital component of securing remote desktop connections. It ensures that data transmitted between the user’s device and the remote server is protected from interception. Modern protocols like TLS 1.2 and TLS 1.3 are widely used to secure remote desktop sessions. For example, RDP (Remote Desktop Protocol) relies on encryption to safeguard user credentials and session data. However, if encryption is not properly configured or if the protocol is outdated, the connection can be vulnerable. When choosing an encryption method, consider factors like algorithm strength, key length, and protocol compatibility. A table below compares popular encryption protocols used in remote desktop security to help you make an informed decision. | Encryption Protocol | Strength | Key Length | Common Use Cases | |———————-|———|———-|——————| | TLS 1.2 | Moderate | 256 bits | Legacy systems | | TLS 1.3 | High | 256 bits | Modern RDP | | AES-256 | High | 256 bits | Data at rest | | RSA 2048 | Moderate | 2048 bits | Authentication | Securing User Authentication User authentication is another critical aspect of remote desktop security. Strong authentication protocols, such as two-factor authentication (2FA), add an extra layer of protection against unauthorized access. For example, using a password combined with a time-based one-time password (TOTP) can significantly reduce the risk of brute-force attacks. In addition to 2FA, implementing role-based access control (RBAC) ensures that users have access only to the resources they need. This approach not only simplifies management but also limits the potential damage if a user’s credentials are compromised. By combining these methods, you can create a more secure environment for your remote desktop sessions. Network Security Measures The network you use to connect to a remote desktop plays a crucial role in its security. Public networks, such as those in cafes or airports, are more susceptible to attacks like man-in-the-middle (MITM) and eavesdropping. To mitigate these risks, always use a secure Virtual Private Network (VPN) when connecting from public Wi-Fi. A VPN encrypts your internet traffic and hides your IP address, making it harder for attackers to intercept your data. Another network security measure is firewall configuration. By setting up rules to allow only specific traffic through the firewall, you can prevent unauthorized access to your remote desktop. Additionally, network segmentation helps isolate remote access from the rest of the network, reducing the attack surface. These strategies work together to create a layered defense against potential threats. Steps to Secure a Remote Desktop Connection Securing a remote desktop connection requires a combination of technical and procedural measures. By following these steps, you can significantly reduce the risk of unintended access and ensure that your remote sessions remain safe and reliable. Use Strong Passwords and Credential Management One of the simplest yet most effective ways to secure a remote desktop connection is by using strong, unique passwords. A strong password typically includes a mix of uppercase and lowercase letters, numbers, and special characters. Avoid using default passwords or those that are easy to guess, such as “password123” or “admin.” In addition to strong passwords, credential management is essential. Tools like password managers can store your credentials securely and generate complex passwords automatically. This not only enhances security but also reduces the risk of password reuse across multiple accounts. For instance, if a hacker gains access to one of your passwords, they can’t automatically access all your other systems if they are unique. Enable Two-Factor Authentication (2FA) Two-factor authentication (2FA) adds an extra layer of security by requiring users to provide two forms of identification before accessing the remote desktop. This could include a password and a one-time code sent to a mobile device, a biometric scan, or a hardware token. Enabling 2FA can prevent brute-force attacks and unauthorized access even if a password is compromised. Many remote desktop services, such as Microsoft Remote Desktop and TeamViewer, offer built-in 2FA options. By setting up 2FA, you ensure that even if someone steals your password, they can’t log in without the second authentication factor. This is especially