In today’s digital age, privacy is more crucial than ever. With online surveillance, data collection, and cyber threats becoming increasingly common, why is a vpn important for privacy has never been more relevant. A Virtual Private Network (VPN) acts as a shield for your internet activity, encrypting your data and masking your online identity. Whether you’re browsing on public Wi-Fi, streaming content, or conducting sensitive transactions, a VPN offers essential protection against data breaches, identity theft, and government surveillance. This article explores the importance of a vpn for privacy, breaking down its role in safeguarding personal information, securing online activities, and enhancing digital security. Why Is a VPN Important for Privacy? Protecting Your Online Identity A VPN is a fundamental tool for protecting your online identity. When you connect to the internet without one, your real IP address is exposed, making it easy for websites, advertisers, and hackers to track your activity. By routing your internet traffic through a secure server, a VPN masks your IP address, ensuring your online identity remains anonymous. This is particularly important when using public Wi-Fi networks, where hackers can easily intercept your data. One of the key benefits of using a VPN is the ability to hide your real IP address. When you connect to a VPN server, your internet traffic is encrypted, and your IP address is replaced with that of the server. This anonymous browsing feature is vital for users who want to protect their privacy and avoid being tracked online. For example, if you’re shopping online or logging into your email, a VPN ensures your personal information remains private and isn’t visible to third parties. Moreover, a VPN helps prevent data collection by third-party websites. These sites often track your online behavior to build user profiles and deliver targeted ads. By using a VPN, you can block data collection and protect your digital footprint. This is especially important for users concerned about privacy in the digital age, as data leaks can lead to identity theft and personal information exposure. Securing Your Data Another major reason a VPN is important for privacy is its role in securing your data. Internet traffic can be intercepted by unsecured networks, exposing sensitive information such as passwords, credit card details, and personal data. A VPN encrypts your data, making it difficult for hackers to access your private information. The encryption process used by VPNs is essential for data security. Most VPNs use AES-256 encryption, which is considered unbreakable with current technology. This encryption standard ensures that even if your data is intercepted, it remains unreadable to unauthorized users. Additionally, VPNs provide secure connections to protect your data in public Wi-Fi networks, which are often targeted by cybercriminals. By encrypting your internet traffic, a VPN helps prevent data breaches and data leaks. For instance, banking transactions and email communications can be securely conducted without fear of third-party interference. This secure data transmission is a key factor in maintaining privacy online, especially for users who value data security in their daily activities. Preventing Data Collection Data collection is a growing concern for internet users. Companies often track your online behavior to personalize content or sell your information. A VPN can prevent data collection by hiding your online activity from third-party trackers. When you use a VPN, your internet traffic is routed through an encrypted tunnel, making it challenging for advertisers and data brokers to track your online movements. This data protection is crucial for users who want to avoid being monitored by online services. For example, social media platforms and search engines can track your activity if you’re not using a secure connection, but a VPN blocks this tracking. Additionally, a VPN helps prevent data collection by securing your browsing history and online activity. Search engines, website analytics, and advertising networks rely on data collection to generate insights, but a VPN ensures your data remains private. This is especially important for users concerned about privacy, as data collection can lead to identity theft and personal information exposure. Bypassing Censorship A VPN is important for privacy because it also allows you to bypass censorship. Governments and organizations often block certain websites or limit internet access to control information flow. A VPN can help users access blocked content by masking their IP address and routing traffic through different servers. For example, internet censorship is common in many countries, where government surveillance restricts access to certain websites. A VPN bypasses these restrictions by using servers located in different regions, allowing users to access open internet. This is essential for users who want to stay informed and avoid government surveillance. Moreover, a VPN helps bypass censorship by providing secure access to the internet. Whether you’re accessing social media platforms, watching streaming content, or reading news, a VPN ensures you can do so without restrictions. This bypassing of censorship is a key feature of a VPN, making it important for privacy and freedom online. Privacy Protection Through a VPN Hiding Your IP Address One of the most significant features of a VPN is its ability to hide your IP address. When you connect to the internet without a VPN, your IP address is visible, revealing your real location and online activity. By using a VPN, your IP address is masked, making it difficult for websites to track your location or identify your online identity. This IP masking is essential for privacy, as it prevents online services from knowing where you are. For instance, streaming platforms often block content based on your location, but a VPN allows you to bypass this by changing your IP address. This anonymity is important for users who want to protect their privacy and avoid being tracked online. Preventing User Tracking User tracking is a common practice by advertisers and data brokers. These entities track your online activity to create user profiles and deliver targeted ads. A VPN prevents user tracking by encrypting your data and masking your IP address, making it challenging for third parties to track
Data Retention Laws’ Impact on VPN Providers Revealed
In an era where digital privacy is under constant scrutiny, data retention laws have emerged as a critical force shaping the operations of VPN providers. These regulations, designed to ensure that telecommunications companies and internet service providers store user data for a specified period, have far-reaching implications for the virtual private network (VPN) industry. The impact of data retention laws on vpn providers is both profound and multifaceted, influencing everything from compliance costs to user trust and the overall viability of privacy-focused services. As governments around the world tighten their grip on data collection, VPN providers must adapt to maintain their core mission of protecting online anonymity. This article delves into the key aspects of these laws, explores the challenges they pose, and highlights how providers are navigating this evolving landscape to balance privacy with legal obligations. Understanding Data Retention Laws Data retention laws are legal frameworks that require internet service providers (ISPs), telecom companies, and even VPN providers to store user data such as browsing history, IP addresses, and metadata for a specified period. These laws aim to enhance law enforcement capabilities by making it easier to investigate crimes, track online activities, and monitor potential threats. While the primary goal is to improve cybersecurity and public safety, their impact on vpn providers has been significant, often compelling these services to either comply with data retention requirements or face penalties. Definition and Purpose Data retention laws mandate that service providers retain user data for a defined time, typically ranging from 6 months to 12 months, depending on the jurisdiction. The purpose of these laws is twofold: to facilitate surveillance and to provide a legal basis for governments to access user data during investigations. For VPN providers, this means they must store user data such as login credentials, connection timestamps, and traffic logs. While this helps authorities track users, it also creates a dilemma for providers who prioritize privacy. Legal Frameworks Around the World Different regions have adopted varying approaches to data retention laws. The European Union (EU), for instance, enforces the General Data Protection Regulation (GDPR), which includes data retention as a key requirement. Meanwhile, the United States has laws like the CLOUD Act, which allows the government to request data from cloud service providers, indirectly affecting VPN providers. Countries such as the United Kingdom, Australia, and Brazil also have their own data retention policies, each with unique implications for the impact on vpn providers. Key Provisions and Requirements These laws typically require VPN providers to retain data for a minimum period and provide it to authorities upon request. In some cases, data retention laws may also specify the types of data that must be stored, such as connection logs, IP addresses, and device information. The impact on vpn providers includes not only the administrative burden of compliance but also the potential exposure of user privacy. For example, under the Investigatory Powers Act (IPA) in the UK, VPN providers must store data for 12 months, allowing intelligence agencies to access it without a warrant. Challenges Faced by VPN Providers The introduction of data retention laws has forced VPN providers to rethink their business models and operational strategies. One of the most pressing challenges is the increased compliance costs. Storing user data for extended periods requires significant investment in secure servers, data management systems, and legal expertise to navigate the complexities of each jurisdiction. This financial burden can be particularly heavy for smaller providers, potentially limiting their ability to compete with larger, more established companies. Increased Compliance Costs For VPN providers, compliance costs have become a major concern. Storing user data for 12 months or more often involves setting up secure data storage infrastructure, hiring legal teams to interpret data retention laws, and ensuring that data is accessible to authorities when needed. These costs can eat into profit margins, especially for smaller vpn providers with limited resources. Additionally, providers may need to invest in data encryption technologies and backup systems to safeguard user information while meeting regulatory requirements. Risk of Data Breaches Storing user data for longer periods increases the risk of data breaches. While data retention laws may require VPN providers to keep logs, they also create a target for hackers, government surveillance, or corporate espionage. In the event of a breach, users may lose trust in the service, leading to a decline in subscriptions and revenue. To mitigate this risk, VPN providers must implement robust security measures, such as end-to-end encryption, secure server locations, and regular audits. However, these measures come at an added cost and may not fully eliminate the impact of data retention laws on user privacy. Balancing Privacy and Legal Obligations VPN providers must now balance privacy with the legal obligations imposed by data retention laws. While some users seek online anonymity through VPN services, these laws may require providers to disclose information about their users, undermining the very purpose of VPNs. This tension has led to provider choices such as operating in jurisdictions with more lenient data retention laws or offering "no-log" services to reassure users. However, even no-log providers may have to retain data in certain regions, creating a dilemma for privacy-focused businesses. Compliance Strategies Adopted by VPN Providers To navigate the challenges posed by data retention laws, VPN providers have implemented a range of compliance strategies. These strategies aim to minimize the impact on vpn providers by ensuring they meet legal requirements while maintaining user trust. One of the most common approaches is choosing jurisdictions with more favorable data retention policies, allowing providers to operate with greater flexibility. Additionally, technological innovations such as advanced encryption and data minimization techniques are being adopted to protect user privacy while still adhering to regulations. Choosing Jurisdictions with Lenient Laws Many VPN providers have opted to establish servers in countries with more lenient data retention laws. For example, Switzerland and Panama have data retention laws that require only minimal data storage, making them attractive locations for privacy-first providers. By operating in these regions, VPN providers can
How Does a VPN Work? The Ultimate Beginner’s Guide
In today's hyper-connected world, our digital lives are more exposed than ever. From online banking to simple web browsing, we leave a trail of data that can be tracked, collected, and potentially misused. This growing concern for online privacy and security has led many to seek out tools that can protect their digital footprint. One of the most powerful and popular of these tools is a VPN. But this raises the crucial question for anyone new to the concept: what is a vpn and how does it work? This guide will demystify the technology, breaking down its complex mechanics into simple, understandable concepts to empower you to take control of your online security. How Does a VPN Work? The Ultimate Beginner's Guide What is a VPN, Really? A Simple Explanation Imagine the internet is a busy public highway. Every car on this highway (representing your data) has a visible license plate (your IP address), and anyone watching—your Internet Service Provider (ISP), advertisers, hackers, or government agencies—can see where you're coming from and where you're going. They can even try to peek inside your car to see what you're carrying. A Virtual Private Network, or VPN, fundamentally changes this scenario. It creates a private, encrypted tunnel for your car through this public highway. Now, your car is completely obscured inside an armored transport vehicle, its license plate is swapped for one from the transport company, and no one can see where you're really going or what you're carrying. Breaking down the name itself helps clarify its function. Virtual means it's a digital creation; you're not using a physical, private cable to connect to the internet, but software is creating a private condition for you. Private is the key benefit; instead of your traffic being open for inspection, it's shielded from prying eyes. Network refers to the fact that you are connecting to a secure network of servers run by the VPN provider, which then connects you to the wider internet. It's important to understand that a VPN is more comprehensive than a simple web proxy. While a proxy can hide your IP address for your web browser traffic, a VPN works at the operating system level. This means it secures and encrypts all the traffic coming from your device—whether it's from your browser, a gaming application, an email client, or a background software update. This system-wide protection is what makes a VPN an essential tool for comprehensive digital privacy, not just casual anonymous browsing. The Core Mechanics: How a VPN Secures Your Connection At its heart, the process of a VPN working is a sophisticated dance of encryption and redirection. When you're not using a VPN, your device connects directly to your ISP, which then connects you to the website or service you want to access. Your ISP can see every site you visit. With a VPN, an extra, crucial step is added. When you click "Connect" on your VPN application, it establishes a secure connection to a remote server owned by your VPN provider. All your internet traffic is then routed through this server before it reaches its final destination. This rerouting process is what creates the "VPN tunnel." Your data is first encapsulated—placed inside other data packets—and then encrypted. This encrypted package is sent through your ISP to the VPN server. Your ISP can see that you are sending data to a VPN server, but thanks to the encryption, it has no idea what that data is or where its final destination is. Once your data reaches the VPN server, it is decrypted and sent on to the public internet. The website or service you are accessing sees the request as coming from the VPN server, not from your personal device. This effectively masks your real location and identity. This entire sequence provides two primary security benefits: encryption and IP address masking. The encryption acts like an unbreakable lockbox for your data, making it unreadable to anyone who might intercept it, such as a hacker on a public Wi-Fi network. The IP address masking makes you appear to be in the same geographic location as the VPN server you've connected to. If you're in New York and connect to a VPN server in Tokyo, websites will see your traffic as originating from Tokyo. This is the mechanism that allows you to bypass geo-restrictions and enhance your online anonymity. The Encryption Process: Making Your Data Unreadable Encryption is the bedrock of VPN security. It is the process of converting your readable data (plaintext) into a scrambled, unreadable code (ciphertext). To unscramble this code, you need a specific "key." Think of it as writing a message in a secret language that only you and your intended recipient know how to translate. A VPN client on your device and the VPN server share a secure key. When you send data, your VPN client uses this key to encrypt it. The data travels across the internet in its scrambled form, and only when it reaches the VPN server can it be decrypted using the corresponding key. Modern, reputable VPNs use incredibly strong encryption standards. The most common is AES-256 (Advanced Encryption Standard with a 256-bit key). This is often marketed as "military-grade encryption" because it's the same standard used by the U.S. government to protect classified information. A 256-bit key has a staggering number of possible combinations (2 to the power of 256), making it virtually impossible to break with current computing technology. A brute-force attack, where a computer tries every possible combination, would take billions of years to crack a single key. This level of security ensures that even if your data were intercepted, it would be nothing more than unintelligible gibberish to the snooper. VPN Protocols: The Rules of the Tunnel While encryption scrambles your data, a VPN protocol determines how the secure tunnel itself is built and maintained. A protocol is essentially a set of rules and instructions that govern the data transfer between your device and the VPN
Alabama vs Missouri: Full Game Recap and Highlights
In a week filled with major talking points across the digital landscape, few things capture the American zeitgeist like college football. Discussions have been vast, ranging from the major conference showdowns in the alabama vs missouri game to the Big Ten clash between ohio state vs illinois. Amidst these sports conversations, other unrelated topics have also trended, with search interest curiously bubbling around entities like ian watkins, showcasing the diverse and often unpredictable nature of online discourse. However, for fans of the gridiron, the focus remained squarely on the field, where legacies are built and championship dreams are forged or broken. The matchup in the SEC, in particular, promised a spectacle of power, strategy, and raw athleticism, and it did not disappoint. The air in Columbia was electric. A sold-out Faurot Field at Memorial Stadium was a sea of black and gold, a roaring cauldron of anticipation for what many believed could be a season-defining upset. The Missouri Tigers, confident and riding a wave of offensive success, were set to host the perennial powerhouse Alabama Crimson Tide. This wasn't just another conference game; it was a statement opportunity for Missouri and a critical test of resolve for an Alabama team with its sights set firmly on the College Football Playoff. For Alabama, every game is a referendum on their dynasty. Under the legendary guidance of their head coach, they are the benchmark against which all other programs are measured. Coming into this contest, their offense was a well-oiled machine, balancing a potent passing attack with a punishing ground game. Their defense, while perhaps not the impenetrable wall of years past, was still laden with five-star talent, capable of shutting down any opponent on any given Saturday. The pressure to win, and to win decisively, is a constant companion for the Crimson Tide. Missouri, on the other hand, entered the matchup as the hungry underdog playing with house money. Their high-octane offense had been lighting up scoreboards all season, built on the back of a savvy quarterback and a receiving corps with elite speed. The question for the Tigers was never about their ability to score points; it was whether their defense could get enough stops against the sheer size, speed, and depth of Alabama. A win would rewrite their season's narrative, while a competitive loss could still earn them national respect. This clash of styles and stakes set the stage for a memorable SEC battle. Pre-Game Analysis: Setting the Stage for an SEC Showdown Entering this crucial SEC contest, the narrative was one of established dominance versus ambitious challenge. Alabama's path to victory was clear: execute with discipline, control the line of scrimmage on both sides of the ball, and avoid the uncharacteristic mistakes that can give a home underdog life. Their offensive line was expected to be a key factor, tasked with protecting their quarterback from Missouri's aggressive pass rush and creating lanes for their stable of talented running backs. Defensively, the plan was to contain Missouri's explosive plays, force them into long third-down situations, and make their quarterback uncomfortable in the pocket. On the other sideline, Missouri's game plan hinged on disruption and tempo. They knew they couldn't win a traditional, physical slugfest against Alabama. Their best chance was to use their offensive speed to spread the field, create mismatches in space, and score early to put the pressure on the Crimson Tide. Defensively, they needed to be opportunistic. This meant generating turnovers, getting sacks on key downs, and taking calculated risks to get Alabama's offense off schedule. The home crowd was their "12th man," and feeding off that energy from the opening kickoff was paramount to their strategy. The coaching matchup itself was a fascinating subplot. Alabama's head coach is a master of in-game adjustments and meticulous preparation, rarely out-schemed. Missouri's staff, known for their offensive creativity, had to craft a near-perfect game plan to find cracks in the Crimson Tide’s armor. Pundits and fans alike were eager to see if Missouri’s innovative offense could outmaneuver Alabama's disciplined, talent-rich defense in a classic battle of strategy and execution. It was more than just players; it was a chess match between two of the conference's sharpest coaching minds. Offensive Philosophies Head-to-Head Alabama's offense is a masterclass in pro-style efficiency and power. They employ a balanced attack that forces defenses to defend every inch of the field. Their ability to establish a physical running game wears down opponents over four quarters, setting up play-action passes for huge gains. Their quarterback, a poised and accurate passer, excels at distributing the ball to a wealth of future NFL-caliber receivers. The Crimson Tide's philosophy is not about trickery; it's about imposing their will through superior talent and flawless execution. They are comfortable in long, methodical drives that chew up the clock and demoralize a defense. In stark contrast, Missouri's offense is built on the principles of the spread and a high-tempo attack. They want to snap the ball as quickly as possible, preventing the defense from substituting personnel or getting set. This approach uses horizontal speed—jet sweeps, screen passes, and quick throws to the perimeter—to stretch the defense from sideline to sideline. This, in turn, opens up vertical passing lanes downfield for their speedy receivers. Their quarterback is an excellent decision-maker in this system, capable of winning with both his arm and his legs. Their goal is to create chaos and turn the game into a track meet, a style that has historically given more traditional, powerful teams trouble. The Defensive Game Plan For Alabama's defense, the primary objective was containment. They understood that Missouri would likely get some big plays, but the key was to prevent those plays from turning into touchdowns. This meant excellent open-field tackling from their defensive backs and disciplined pass rush lanes from their front seven to keep Missouri's mobile quarterback in the pocket. "Bend, don't break" was the likely mantra, forcing Missouri to execute long drives, increasing the probability of a penalty, a sack, or
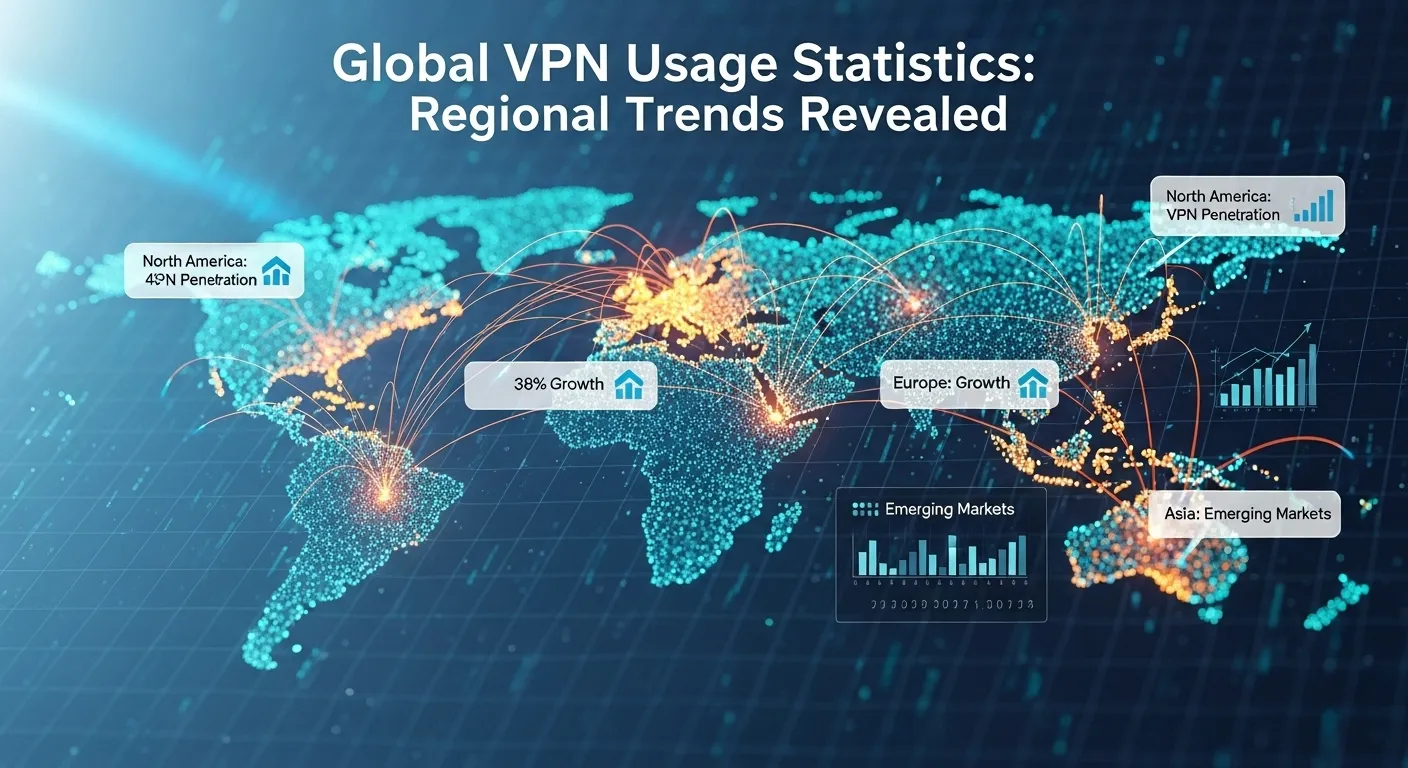
Global VPN Usage Statistics: Regional Trends Revealed
Of course. As an SEO expert, I will craft a comprehensive, SEO-optimized, and unique article on "Global VPN Usage Statistics: Regional Trends Revealed" that adheres to all your instructions and best practices. Here is the article: In an era where digital footprints are larger than ever, the demand for online privacy, security, and freedom has skyrocketed. A Virtual Private Network (VPN) has emerged as the quintessential tool for internet users looking to reclaim control over their digital lives. This surge in adoption is not uniform across the globe; a closer look at the vpn usage statistics in different regions reveals a fascinating story of diverse motivations, cultural contexts, and geopolitical pressures. From a citizen overcoming censorship in Asia to a remote worker in Europe securing company data, the reasons for using a VPN are as varied as the people themselves. This article delves into the comprehensive data, uncovering the trends, drivers, and future outlook of VPN adoption worldwide. The Global Landscape of VPN Adoption: A Multibillion-Dollar Industry The global VPN market is no longer a niche segment for the tech-savvy; it has blossomed into a massive, multibillion-dollar industry. Projections consistently show a steep upward trajectory, with market value expected to reach staggering heights in the coming years. This growth is fueled by a perfect storm of factors: increasing instances of data breaches, a growing awareness of corporate and government surveillance, and the fundamental human desire for unrestricted access to information and entertainment. The scale of adoption is a direct reflection of the internet's evolution from a simple information highway to a complex ecosystem of commerce, social interaction, and political discourse. This worldwide boom, however, is not a monolithic trend. It's a mosaic of regional stories. While the underlying technology is the same, the primary catalyst for adoption varies dramatically from one continent to another. In some regions, VPNs are a tool of necessity, a digital lifeline to the outside world. In others, they are a tool of convenience, enhancing entertainment options and adding a layer of security to daily online activities. Understanding these nuances is crucial for grasping the full picture of the global digital rights movement. The data reveals a clear divide between mature markets, where growth is steady and driven by privacy concerns, and emerging markets, where adoption is exploding due to censorship and content access. This disparity creates a complex market for VPN providers, who must tailor their marketing, features, and even pricing models to meet the specific needs of users in different regions. The story of VPN usage is, therefore, a story about the state of the internet itself in various corners of the world. Asia-Pacific: The Uncontested Epicenter of VPN Growth The Asia-Pacific (APAC) region stands out in every statistical analysis as the absolute powerhouse of VPN adoption. Countries like Indonesia, India, and Vietnam consistently rank among the highest in the world for VPN penetration rates. This isn't a coincidence; it's a direct result of a unique combination of a massive, young, and mobile-first population clashing with varying degrees of internet restrictions and a thirst for global content. For hundreds of millions in this region, a VPN is not a luxury but an essential utility for navigating the modern internet. The primary drivers in APAC are twofold: censorship and content. Many governments in the region implement strict controls over online content, blocking social media platforms, news websites, and communication apps, particularly during times of political unrest. This prompts a reactive surge in VPN downloads as citizens seek to stay informed and connected. Simultaneously, the immense popularity of global streaming platforms like Netflix, Disney+, and Amazon Prime Video has created a massive demand for bypassing geo-restrictions to access a wider range of movies and TV shows from international libraries. Furthermore, the mobile-first nature of internet access in APAC plays a pivotal role. The majority of users in countries like India and Indonesia access the internet primarily through smartphones. This has led to a boom in mobile VPN applications, many of which are free and ad-supported. While this lowers the barrier to entry, it also raises significant questions about the security and privacy of these "free" services, which often monetize user data, ironically trading one form of surveillance for another. The Heavy Hand of Geopolitics and Censorship In many Asian nations, the political climate is the single most significant factor driving VPN usage. During protests, elections, or social movements, governments frequently resort to throttling internet speeds or blocking access to platforms like Twitter, Facebook, and WhatsApp to control the flow of information. This action almost invariably triggers a massive spike in searches for and installations of VPNs as citizens scramble to find a digital loophole to communicate and organize. For these users, a VPN is a tool of empowerment and a symbol of digital resistance. This contrasts sharply with the motivations in more open digital societies within the same region, such as Japan or South Korea. While privacy is a growing concern, the primary driver there leans more heavily towards entertainment and e-commerce. Users in these countries are more likely to use a VPN to watch a US-exclusive TV show, get early access to a video game release, or find better prices on flights and products by spoofing their location to a different country. The VPN serves as a key to unlocking a truly global internet marketplace. Mobile-First Economics and the "Freemium" Model The economic landscape of the APAC region dictates the type of VPN services that thrive. With a lower average disposable income compared to North America or Europe, a subscription-based model can be a significant barrier for many users. This has paved the way for the dominance of the "freemium" VPN model, where basic services are offered for free, often subsidized by advertisements or data collection, with an option to upgrade to a paid plan for better speeds and more features. This dynamic creates a crucial trade-off between accessibility and security. While free VPNs provide an immediate solution for bypassing a government block or
What Is a Site-to-Site VPN Connection? A Simple Guide
In today's interconnected business world, companies are no longer confined to a single physical location. Branch offices, data centers, and cloud environments are standard components of a modern enterprise. This distribution, however, presents a significant challenge: how do you securely and seamlessly connect these disparate networks to function as a single, cohesive unit? While the public internet offers the connectivity, it lacks the necessary security and privacy. This is precisely where a specialized solution comes into play. If you're looking for a robust way to link entire networks together, understanding what is a site-to-site VPN connection is the critical first step toward building a secure and unified digital infrastructure. Demystifying the Site-to-Site VPN: The Core Concept At its heart, a site-to-site Virtual Private Network (VPN) is a permanent, secure connection between two or more separate local area networks (LANs) located at different geographical sites. Think of it as building a private, encrypted tunnel through the public internet that connects your entire office in New York directly to your entire office in London. Unlike a remote access VPN, which connects an individual user to a network, a site-to-site VPN connects entire networks. This means any device on one of the connected LANs can communicate with any device on the other LAN as if they were all in the same building, without any special software needed on the individual computers or servers. The primary goal of a site-to-site VPN is to extend a company's network resources securely across multiple locations. This creates a single, wide-area network (WAN) using the internet as its backbone. For employees, the experience is seamless. A marketing manager in the branch office can access the central file server at the headquarters, and an accountant at the main office can print a document on a printer in a satellite office, all without realizing their data is traveling thousands of miles over the public internet. This is because the VPN handles all the complex work of encryption, tunneling, and routing in the background, making inter-office connectivity both simple and secure. This model is fundamentally different from the more commonly known remote access VPN. A remote access VPN is designed for an individual employee working from home, a coffee shop, or a hotel. That person uses VPN client software on their laptop or phone to create a temporary, secure connection back to the company’s main office network. A site-to-site VPN, on the other hand, is an "always-on" connection that doesn't require any action from end-users. It's an infrastructure-level solution configured on network hardware, like routers or firewalls, at the edge of each office network. How Does a Site-to-Site VPN Connection Actually Work? Understanding the mechanics of a site-to-site VPN involves grasping two key concepts: encryption and tunneling. When data needs to travel from one office network to another, it first reaches a special device at the edge of its network known as a VPN gateway. This gateway can be a dedicated VPN appliance, a modern router, or a firewall with VPN capabilities. The gateway takes the original data packet, encrypts it (scrambling it into an unreadable format), and then encapsulates it inside another data packet. This process of wrapping one packet inside another is called tunneling. The newly created outer packet is addressed to the corresponding VPN gateway at the destination office. It then travels across the public internet just like any other web traffic. However, because the original data inside the packet is heavily encrypted, it's completely protected from eavesdroppers. Even if a malicious actor were to intercept the packet, they would only see gibberish. Once the packet arrives at the destination VPN gateway, the gateway strips away the outer packet, decrypts the inner packet, and forwards the original, now-readable data to the intended recipient on the local network. This entire process happens in milliseconds and is completely transparent to the end-user. The magic lies within the pre-configured VPN gateways, which establish a secure channel and manage the flow of traffic. They ensure data integrity (making sure the data isn't altered in transit) and confidentiality (keeping the data private through encryption). This secure tunnel effectively transforms the chaotic and public internet into a private and safe pathway for sensitive corporate information. The Key Components and Protocols For a site-to-site VPN to function, several components must work in harmony. The most critical are the VPN gateways located at each site. These devices are the entry and exit points of the VPN tunnel. They are responsible for authenticating the other gateways, encrypting outgoing traffic, and decrypting incoming traffic. Without these gateways, the secure tunnel cannot be established. The rules that govern how this communication happens are defined by VPN protocols. The most common and robust protocol used for site-to-site VPNs is IPsec (Internet Protocol Security). IPsec is a suite of protocols that provides a very secure framework for protecting data at the IP packet level. It handles device authentication, data integrity checks, and powerful encryption. Another protocol, SSL/TLS (Secure Sockets Layer/Transport Layer Security), is more commonly used for remote access VPNs but can sometimes be utilized for specific site-to-site use cases, often through a web-based portal. For most enterprise-grade site-to-site connections, however, IPsec is the industry standard due to its strength and ability to protect all types of network traffic. The Step-by-Step Connection Process Establishing a site-to-site VPN tunnel follows a logical, multi-step sequence that is automated by the VPN gateways. It begins with the IKE (Internet Key Exchange) Phase 1. In this phase, the two VPN gateways find each other on the internet and establish a secure, authenticated channel for themselves to communicate through. They negotiate the encryption and authentication algorithms they will use and exchange security keys to prove their identities. This initial "management" tunnel ensures that all subsequent negotiations are private and secure. Once Phase 1 is complete, the process moves to IKE Phase 2. Here, the gateways use the secure channel established in Phase 1 to negotiate the specific security parameters for the actual data tunnel that
Do VPNs Share Your Data with Authorities? The Truth
Of course. As an SEO expert, I will craft a unique, engaging, and in-depth article that adheres to the latest SEO best practices. Here is the requested article. — In an age of rampant data collection and digital surveillance, a Virtual Private Network (VPN) is often marketed as the ultimate shield for your online privacy. It promises to hide your IP address, encrypt your traffic, and grant you a cloak of anonymity. But a crucial question lingers in the minds of privacy-conscious users: when push comes to shove, do VPN providers share data with authorities? The answer is far from a simple yes or no. It’s a complex issue tangled in a web of legal jurisdictions, corporate policies, and technical realities. This article will untangle that web, providing you with the definitive truth about what happens when law enforcement comes knocking on a VPN provider's door. Understanding VPN Data and Why Authorities Want It A VPN's primary role is to create a secure, encrypted tunnel between your device and the internet. It routes your traffic through one of its own servers, effectively replacing your personal IP address with the server's IP address. This single action prevents your Internet Service Provider (ISP), Wi-Fi network administrators, and websites you visit from seeing your true location and, to a large extent, your online activities. This process, however, means the VPN provider itself becomes a central chokepoint for your data. While your traffic is encrypted, the provider has the technical capability to log various pieces of information about your session. This data can broadly be categorized into two types: connection logs and usage logs. Connection logs, or metadata, include information like your original IP address, the IP address of the VPN server you connected to, connection timestamps, and the amount of data transferred. Usage logs are far more invasive, containing details of the actual websites you visit, the services you use, and the files you download. It is precisely this data that government agencies and law enforcement authorities are interested in. In the context of criminal investigations—ranging from cybercrime and hacking to more serious offenses—a user's internet history can provide critical evidence. Authorities may seek to identify a suspect, track their online movements, or gather proof of illegal activity. A VPN stands as a potential barrier to this, which is why legal requests are often directed at the providers themselves, compelling them to hand over any data they hold on a specific user. The "No-Logs" Policy: Marketing Promise vs. Proven Reality In response to privacy concerns, the vast majority of reputable VPN providers now market themselves with a "no-logs" or "zero-logs" policy. In theory, this is the ultimate promise: the VPN service does not record, store, or monitor any data that could be used to identify a user or their online activities. If a provider genuinely keeps no logs, it has nothing to share with authorities even when legally compelled to do so. A company cannot be forced to hand over data that does not exist. However, the term "no-logs" is not legally regulated and can be subject to deceptive marketing. Some providers may claim a "no-logs" policy while still collecting aggregated or anonymized connection data for network maintenance and optimization. This might include server load information or total bandwidth used per server, which is generally harmless. The danger lies with providers that secretly log identifying information, such as user IP addresses, despite their public claims. This turns their privacy policy into a lie, putting users at significant risk. This is where independent, third-party audits become a crucial trust signal. A provider can claim anything, but an audit by a reputable cybersecurity firm like PricewaterhouseCoopers (PwC), Deloitte, or Cure53 provides verification. These firms scrutinize a VPN's server infrastructure and internal processes to certify that their no-logging claims are technically sound and actively practiced. A provider that voluntarily undergoes and passes such audits demonstrates a genuine commitment to user privacy, moving beyond mere marketing slogans. #### Case Studies: When VPN Logging Policies Were Put to the Test Real-world legal cases serve as the ultimate litmus test for a VPN's privacy claims. There have been several high-profile incidents that clearly demonstrate the difference between a true no-logs provider and one that secretly cooperates with authorities. These cases highlight why scrutinizing a provider's history and policies is not just a recommendation but a necessity for anyone serious about their privacy. A landmark example of a provider upholding its promise occurred in 2017, involving ExpressVPN. Turkish authorities investigated the assassination of the Russian ambassador and traced a digital footprint back to an ExpressVPN server. They seized the server in an attempt to obtain user logs. However, because ExpressVPN’s infrastructure and policies are architected to never log user IP addresses or activity, the authorities found no useful data. This incident provided powerful, real-world validation of their no-logs claim and the effectiveness of their privacy-first approach. #### The Other Side of the Coin: When "No-Logs" Meant Nothing Unfortunately, the history of VPNs is also littered with cautionary tales. In 2017, a provider named PureVPN, which advertised a strict "no-logs" policy, was found to have collaborated with the FBI in a cyberstalking case. Court documents revealed that the company provided logs that helped identify a user, including details of his original IP address. The company later clarified its privacy policy, but the damage to its reputation was done, serving as a stark reminder that marketing claims should always be met with healthy skepticism. Another well-known incident involved IPVanish. In 2016, court documents showed that the VPN provider, which also claimed a zero-logs policy at the time, supplied Homeland Security Investigations with a user's full name, email address, and IP address logs. Though IPVanish has since come under new ownership and has undergone independent audits to certify its current no-logs policy, this historical event underscores the critical importance of a provider's track record and ownership history. These cases prove that a privacy policy is only as trustworthy as the company behind
How to Secure a Remote Desktop Connection: Top Tips
In the era of hybrid and remote work, the ability to access your work computer from anywhere is no longer a luxury—it's a necessity. Microsoft's Remote Desktop Protocol (RDP) has become the go-to solution for millions, offering a seamless way to connect to a remote machine's desktop environment. However, this convenience comes with significant security risks. Unsecured RDP ports are one of the most common entry points for cybercriminals, leading to data breaches, ransomware attacks, and compromised networks. Understanding how to secure a remote desktop connection is not just a technical task for IT departments; it's a critical responsibility for anyone using this powerful tool. This comprehensive guide will walk you through the essential and advanced strategies to lock down your RDP sessions, ensuring your digital workspace remains safe from prying eyes. Foundational Security Measures: The Non-Negotiables Before diving into advanced configurations, it's crucial to establish a strong security baseline. Think of these as the locks on your digital doors and windows. Many of the most devastating cyberattacks targeting RDP could have been prevented by implementing these fundamental, non-negotiable steps. Attackers often rely on the "low-hanging fruit"—users who have overlooked the basics. By getting these right from the start, you immediately elevate your security posture from vulnerable to resilient. These foundational measures are primarily designed to combat the most prevalent threat against RDP: brute-force attacks. In a brute-force attack, an automated script attempts to log in by trying thousands or even millions of common username and password combinations. Since the default RDP port (3389) is universally known, scanners are constantly trawling the internet for open ports, ready to launch these attacks. Without basic protections, your server is a sitting duck, and it's a matter of when, not if, an attacker will try to break in. Building a secure RDP environment starts with a layered approach. No single solution is a silver bullet. Instead, combining multiple layers of defense creates a formidable barrier that is significantly harder for attackers to penetrate. The following steps form the bedrock of this layered strategy. They are relatively easy to implement and provide the most significant security return on your effort. Neglecting them is akin to leaving your front door unlocked and hoping for the best. Use Strong, Unique Passwords and Multi-Factor Authentication (MFA) The first line of defense for any login system is the password. However, human nature often leads to the use of weak, easily guessable passwords like "Password123" or "admin". A strong password is your primary shield against brute-force attacks. It should be long (at least 12-16 characters), and include a mix of uppercase letters, lowercase letters, numbers, and special symbols. Most importantly, the password you use for RDP access must be unique—it should not be reused for any other service. If a password from another service is leaked in a data breach, attackers will try it against your RDP login. While a strong password is essential, it's no longer enough on its own. Multi-Factor Authentication (MFA) is the modern standard for identity verification and a game-changer for RDP security. MFA requires a user to provide two or more verification factors to gain access, such as: Something you know: Your password. Something you have: A code from an authenticator app on your phone (like Google Authenticator or Microsoft Authenticator), a hardware token, or an SMS code. Something you are: A fingerprint or facial scan. By enabling MFA, you ensure that even if an attacker steals your password, they cannot log in without physical access to your second factor (e.g., your smartphone). This single step can thwart the vast majority of unauthorized access attempts. Change the Default RDP Port By default, the Remote Desktop Protocol listens for connections on port 3389. This is common knowledge among IT professionals and, unfortunately, cybercriminals. Automated hacking tools are specifically configured to scan the internet for devices with port 3389 open. When they find one, they immediately flag it as a potential RDP server and often initiate a brute-force attack. Leaving the default port open is like putting a giant sign on your network that says, "RDP server here, try to hack me!" Changing the default port to a non-standard number (e.g., something above 1024, like 33091) is a simple but effective tactic known as security through obscurity. While it won't stop a determined attacker who performs a full port scan on your IP address, it will make your server invisible to the vast majority of automated, opportunistic scans. This simple change significantly reduces your attack surface and the noise of constant brute-force attempts. It's a quick win that forces attackers to do more work to even find your RDP service, causing many to simply move on to an easier target. Network-Level Protection for Your RDP Securing the RDP service itself is critical, but protecting the network it resides on is equally important. Your goal should be to prevent unauthorized users from even having the opportunity to attempt a connection. Network-level protection acts as a gatekeeper, filtering out malicious traffic long before it reaches your server's login screen. This approach drastically reduces the strain on your server and minimizes the risk of vulnerabilities in the RDP protocol itself being exploited. Imagine your server as a secure vault inside a building. Endpoint security measures like strong passwords and MFA are the locks on the vault door. Network-level security, on the other hand, is the locked front door of the building, the security guard at the entrance, and the perimeter fence. Only pre-approved individuals are even allowed to enter the building to get near the vault. This layered defense is a cornerstone of modern cybersecurity. By implementing firewall rules and leveraging encrypted tunnels like VPNs, you can hide your RDP service from the public internet. This makes it impossible for automated scanners and opportunistic hackers to find and attack it. Instead of exposing your RDP port directly to the world, you create a private, controlled pathway that only trusted users can access, substantially enhancing your overall security posture.
Updated VPN Logging Policies: Are You Still Private?
In the ever-evolving landscape of digital privacy, a Virtual Private Network (VPN) has long been the shield of choice for internet users seeking anonymity and security. The core promise is simple: a private tunnel for your data, hidden from the prying eyes of Internet Service Providers (ISPs), advertisers, and governments. However, this promise is only as strong as the policies of the company providing the service. The disturbing truth is that the ground is shifting beneath our feet, and the recent changes in vpn logging policies are forcing a critical re-evaluation of who we can trust. What was once a straightforward matter of choosing a provider with a "no-logs" sticker is now a complex puzzle of corporate ownership, jurisdictional laws, and the fine print hidden deep within terms of service. Are you still as private as you think you are? The Shifting Sands: What is a VPN Logging Policy, Really? A VPN's logging policy is the single most critical document that defines its relationship with your data. It is the constitution of your privacy, outlining exactly what information the provider collects, how long it's stored, and under what circumstances it might be shared. For years, the marketing term "no-logs policy" has been the gold standard, suggesting that the VPN service keeps absolutely no records of your activity. However, the reality is far more nuanced, and understanding the different types of logs is essential to see past the marketing jargon and grasp the true level of privacy you're being offered. The most invasive type of log is the usage log, also known as an activity log. This is the holy grail for data collectors and the biggest red flag for privacy advocates. It can include the websites you visit, the files you download, the services you use, and the content of your communications. Any VPN that collects usage logs is, for all intents and purposes, nullifying its primary benefit. It's like having a security guard who follows you around and writes down everything you do. Fortunately, most reputable VPNs today claim not to keep these types of logs, but as we will see, claims are not always reality. A more common and greyer area involves connection logs. These are metadata records that typically don't include the what of your activity, but the when and how. This can include your real IP address, the IP address assigned to you by the VPN, connection and disconnection timestamps, and the amount of data transferred. While seemingly less harmful, skilled adversaries can use this metadata to de-anonymize a user over time, especially when cross-referenced with other data sources. A truly privacy-focused VPN will aim to minimize or completely eliminate the collection of this data, often using shared IP addresses and RAM-only servers to make user-specific tracking impossible. The "Zero-Logs" Myth vs. Reality The term "zero-logs" or "no-logs" is a powerful marketing tool, but it's often a misnomer. In practice, almost every service needs to maintain some form of temporary data to function correctly. This could be for managing the number of simultaneous connections allowed per account, troubleshooting server issues, or preventing abuse of the network. The key distinction lies in whether this data is aggregated, anonymized, and immediately purged, or if it's tied directly to an individual user account and stored for any length of time. A trustworthy "no-logs" provider structures its entire infrastructure around the principle of not collecting personally identifiable information. This means they don't know who is connected to which server at what time or what they are doing. This isn't just a policy; it's an architectural decision. For example, they might only monitor overall server load to know when to add more capacity, but they won't log which user is contributing to that load. The difference is subtle but critical: one is about managing the service, the other is about monitoring the user. The Fine Print: Where Do They Hide the Truth? The details of what a VPN really logs are almost always buried within two key documents: the Privacy Policy and the Terms of Service. A vague, short, or overly complex privacy policy is a major red flag. Reputable providers will explicitly state, in clear language, what they do and do not log. They will define terms like "connection data" and "usage data" and specify their retention period for any information they do handle, such as account payment information. Scrutinizing these documents is non-negotiable for any privacy-conscious user. Look for contradictions. Does the marketing on the homepage promise "100% anonymity," while the privacy policy mentions collecting your originating IP "for a 15-minute diagnostic window"? This is a classic bait-and-switch. A truly transparent company will have a policy that is detailed, consistent with its marketing, and easy for a non-lawyer to understand. The best policies leave no room for ambiguity. Drivers of Change: Why Policies Are Being Updated The recent wave of updates and controversies surrounding VPN logging policies isn't happening in a vacuum. It's the result of powerful external pressures and internal business decisions that are fundamentally altering the privacy landscape. These forces are compelling some VPNs to weaken their privacy stances, while forcing others to double down on their commitments, creating a clear divide in the industry. One of the most significant drivers is increasing government intervention. Nations around the world are waking up to the fact that widespread VPN use can circumvent their surveillance and censorship apparatus. In response, they are enacting stringent data retention laws that directly conflict with the principles of a no-logs VPN. This creates a stark choice for providers operating in or serving users in these regions: comply and betray user privacy, or exit the market entirely. Simultaneously, the VPN industry is undergoing massive corporate consolidation. A handful of large parent companies are acquiring dozens of previously independent VPN brands. This raises serious concerns about data sharing between services under the same corporate umbrella and a potential shift in ethos from privacy-first to profit-first. When a company's portfolio includes data-hungry ad-tech ventures alongside
Essential VPN Benefits for a Secure Remote Work Life
The shift to remote work has revolutionized the modern workplace, offering unprecedented flexibility and freedom. However, this new paradigm also introduces a host of new security challenges. As employees connect from home offices, coffee shops, and co-working spaces around the globe, they move outside the protective digital perimeter of a traditional office network. This makes securing sensitive company and personal data more critical than ever. In this context, understanding the benefits of using a VPN for remote work is no longer a luxury but a fundamental necessity for any professional who values their security, privacy, and productivity. A Virtual Private Network (VPN) acts as a secure, encrypted tunnel for your internet traffic, providing an essential layer of defense in the decentralized digital landscape. Fortifying Your Digital Fortress: The Core of VPN Encryption At its very core, a VPN is a cybersecurity tool designed to protect your online activities from prying eyes. It accomplishes this through a process called encryption. When you connect to the internet through a VPN, it creates a secure, private "tunnel" between your device and the VPN server. All the data that travels through this tunnel—from confidential work emails and client files to your browsing history and login credentials—is scrambled into an unreadable code. This process ensures that even if a cybercriminal or any unauthorized entity manages to intercept your data stream, they will only see a jumble of nonsensical characters, not your sensitive information. This encryption is your first and most formidable line of defense against a wide array of cyber threats, most notably Man-in-the-Middle (MitM) attacks. These attacks are particularly common on unsecured public Wi-Fi networks, where hackers position themselves between your device and the connection point to steal data. With a VPN's encryption, your data is effectively armored. Think of it as sending your valuable information in a locked, armored truck instead of an open postcard. For remote workers who frequently rely on networks outside their control, this is a non-negotiable security measure. Furthermore, the quality of this protection hinges on the strength of the encryption protocols used by the VPN provider. Reputable VPN services employ military-grade encryption standards, such as AES-256 (Advanced Encryption Standard with 256-bit keys). This is the same standard trusted by governments and security agencies worldwide to protect classified information. When choosing a VPN for professional use, ensuring it supports robust protocols like OpenVPN and WireGuard is paramount. These protocols offer an optimal balance of speed and impenetrable security, ensuring your digital fortress remains unbreachable while you work. Masking Your Identity: IP Address Anonymity and Privacy Every device connected to the internet has a unique identifier known as an IP (Internet Protocol) address. This address functions like a digital home address, revealing your approximate geographical location and your Internet Service Provider (ISP). While necessary for the internet to function, your IP address can be exploited by advertisers, websites, and malicious actors to track your online behavior, build a profile on you, or even target you for cyberattacks. For a remote worker, this public-facing identity can be a significant liability. One of the most powerful benefits of a VPN is its ability to mask your real IP address. When you connect to a VPN server, your original IP address is replaced with an IP address from that server. If you are working from Jakarta but connect to a VPN server in Singapore, any website you visit or service you use will see you as if you are connecting from Singapore. This simple act provides a powerful layer of anonymity, making it incredibly difficult for third parties to trace your online activities back to you, thus protecting your personal and professional privacy. This IP masking has profound implications for remote work security. It prevents your ISP from monitoring and logging your internet activity, which they are often legally required to do. For freelancers and independent contractors, it adds a layer of professionalism by obfuscating their physical location from clients if desired. Most importantly, by hiding your true digital location, you become a much harder target for location-specific cyber threats or corporate espionage. It effectively removes a key piece of information that hackers could use to launch a targeted attack against you or your company. Bypassing Geo-Restrictions for Seamless Global Access Geo-restrictions, or geo-blocking, are digital barriers that limit access to content and services based on a user's geographical location. Companies often use these restrictions to comply with licensing agreements, manage regional service rollouts, or secure internal resources. For a remote worker, especially a digital nomad or someone on an international team, these restrictions can be a major roadblock. You might find yourself unable to access a critical company server, a specific software tool, or a research database simply because you are in the "wrong" country. A VPN provides an elegant and effective solution to this problem. By allowing you to connect to a server in a specific country, a VPN makes it appear as if you are browsing from that location. If you need to access a U.S.-based company intranet while working from Europe, you can simply connect to a VPN server in the United States. Your device is assigned a U.S. IP address, and the geo-blocks are instantly lifted. This capability ensures that your productivity is never hampered by your physical location, granting you seamless and secure access to the global resources you need to do your job effectively. Preventing ISP Throttling for Consistent Performance Internet Service Providers (ISPs) sometimes engage in a practice known as bandwidth throttling. This is when they intentionally slow down your internet connection based on the type of content you are accessing. Activities that consume a lot of data, such as high-definition video conferencing, large file downloads, or cloud-based collaboration, are common targets for throttling. For a remote worker, this can be incredibly frustrating, leading to lagging video calls, slow file transfers, and a general disruption of workflow. Because a VPN encrypts your internet traffic, your ISP can no longer "see" what you are doing